Passwords: First Line of Defense against Identity Theft
Passwords have come a long way since the days of Prohibition, when a knock on the door of a speakeasy required the necessary password for entry and the consumption of illegal liquor. Today, we use passwords and personal identification numbers for just about everything online, in an effort to protect the privacy of our personal information.
Identity theft has grown rampant, proliferating at a time when almost every personal or business transaction passes through one or more computer network. According to the Federal Trade Commission’s latest annual report (covering the 2015 calendar year, with the 2016 report due out in February 2017), there were 480,000 identity theft complaints filed during that time period. Of these, 45% involved tax- or wage-related fraud, 16% involved credit card fraud, 10% involved phone or utilities fraud, 6% involved bank fraud, and 4% involved loan fraud.
One recent report surmised that 15 million Americans have become the victims of identity theft in 2016. That means that 7% of all adults have been victimized in this year alone, with an approximate per-instance loss of $3,500.00. On average, these people spend an additional $500.00 and 30 hours of time trying to recover their identities and make their private information less vulnerable.
Start with Your E-Mail Passwords
My company provides e-mail hosting services through Google and Rackspace for our website hosting clients, and it is rare for a few days to pass without being contacted by a client who has purchased a new computer or mobile device but has misplaced an e-mail account password. For obvious reasons, we do not store those passwords, and we strongly advise our clients to keep records of their passwords in a secure location. Our only option is to assist with changing the lost password, which will then require that passwords be updated on any other actively used devices.
When setting up those e-mail accounts (or updating a password), clients are often annoyed that we will not agree to use a weak password like 123456, abc123, password, passw0rd, qwerty, steelers, yankees, football, baseball, camaro or firebird. (Yes, those are actual passwords that consistently show up on compiled lists of weak passwords.) In fact, Google’s Gmail will not allow an admin to use a password that is made up of fewer than 8 characters (although there are no further password security requirements beyond this minimum length.)
Some people make an attempt at generating a secure password that they can still remember. For example, they might concoct “AIwfCim2ft” from “All I want for Christmas is my 2 front teeth.” The rule of thumb is to use something that is both easy to remember and difficult to guess. This is definitely a step in the right direction, but something totally random that also uses special characters and spaces would be even better, although far less memorable.
Secure passwords will provide a layer of protection against some bad character obtaining your password and hacking into one of your accounts, but they are of far less value in protecting your identity should your account be one of thousands (or millions) compromised in a major data breach.
Hacks Happen
You do not need to be Sony Pictures getting under the skin of Kim Jong Un. Big companies are routinely targeted by hackers from around the globe, putting the security of their subscribers at risk when a breach occurs. In general, big businesses take extraordinary measures to attempt to maintain the utmost security standards, but it is an ongoing game of cat and mouse. For example, Facebook alone has paid out over $5 million to date in its not-highly-publicized Bug Bounty program, where it pays independent “white hat” hackers to identify and repair security vulnerabilities.
That is an example of what one big online business is doing; however your own personal security is to a great degree your own responsibility. You will want to check (and often disable) routinely loose security settings when you buy a new computer or mobile device or when you upgrade one of those to a new operating system. Keep in mind that settings that benefit convenience and ease of use are very often directly at odds with the safeguarding of your personal security.
There are many ways that passwords can be hacked online. The most common technique is the use of dictionary attacks, where commonly used words are highly vulnerable and easily uncovered. Another technique consists of using the brute force of computing power and sophisticated software to run through every possible combination of characters. The more bits of data involved (directly proportional to the number and random nature of characters), the longer it will take to hack a password. Complex character combinations and the use of encryption slow down, but will not prevent, the disclosure of a password to a determined intruder.
There are actually times when a company or individual needs to recover a lost password, and there are other instances where law enforcement needs to crack a password in order to uncover criminal activity. We are all familiar with the FBI vs. Apple Computer encryption debate, involving a cell phone owned one of the shooters in the December 2015 San Bernardino, California terrorist attack. Whether used for good or bad, there are dozens of free, open-source brute force hacking tools that can be easily found and downloaded online. Their existence and ease of access should provide a wake-up call to any computer or mobile device user.
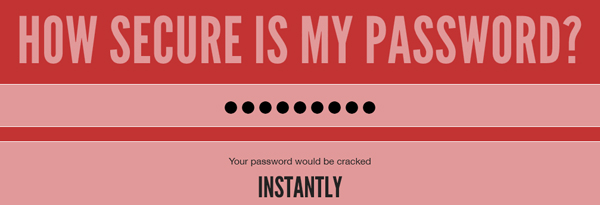
Just in case you think that one of your own passwords is “secure enough”, enter it into this online tool for what will probably be a rude awakening:
https://howsecureismypassword.net/
The minimum standards for password security that are generally considered acceptable today involve the use of at least 12 (preferably 16) entirely random characters (a mix of upper and lower case letters, numbers, spaces and special characters), never including a dictionary word or a repeated sequence, and with no password used in more than one application.
There are several online tools that will assist you in generating secure random passwords. Using one of these tool, I just generated a random 16-character password that I then entered into the secure password test site (shown above.) According to that site, the password that I entered would take 41 trillion years to crack. Here are two such password generator tools. Give one of them a try:
Password Generator
https://passwords-generator.org/
Bitwarden Password Generator
https://bitwarden.com/password-generator/
Storing Passwords
The best advice for keeping track of your cryptic passwords is to always maintain a written paper record in a very secure location. To simplify your life, you can also use one of several password managers that will allow you to encrypt and store all of your passwords in one secure location. You will only have to remember one password to access your files. (If you have been following along and learning from what I have written, that password will meet the standards that I have outlined above.)
The following are some of the best free password managers. They all work across multiple devices. Compare their features and choose one:
Bear in mind that even these password managers are vulnerable to hackers; however, in one documented security breach, only users with weak passwords were impacted. We are over a month into a New Year. Resolve to at least take a step in a positive direction when it comes to your online security.
This post was written by Peter Pelland