Beware the “Sextortion” Scam: A New Form of Cybercrime Making the Rounds
October 28th, 2018
Most people realize that the ultimate in cyberwarfare would be for one country to take down the power grid, telecommunications network, financial industry, or military and defense networks of a foe country. There is no doubt that the United States, Russia, China and other countries maintain this capability but wisely withhold use of this “nuclear option” in cyberwarfare, although there have been instances where the waters have clearly been tested. As has been recently demonstrated, cyberwarfare tends to take a much more subtle and individualized approach, exploiting weaknesses in things like social networks and ballot tabulations. The same sort of approach, where individuals are targeted, is generally practiced in cybercrime, the aggressive bully that is the awkward little stepbrother of cyberwarfare.
Cybercrime takes a variety of forms but generally targets either individuals or individual companies. Small businesses, where there is often only a subtle distinction between a business and its owners, can be particularly vulnerable. In most instances, the criminal activity exploits vulnerabilities in the security practices of the target. These vulnerabilities include the failure to apply software patches and updates, unsecure office practices, and the use of weak, old, and/or repetitive passwords. The results include the easy entry of computer viruses and malware that can turn a computer into a bot on a criminal network or install ransomware that will hold a computer and its files hostage. The same vulnerabilities lead to the proliferation of phishing attempts and other email and telephone scams where the senders or callers impersonate trusted companies in an attempt to obtain passwords, secure information like social security numbers, your credit card numbers, or remote access to your computer.
One of the latest trends in cybercrime exploits a combination of known hacks and personal fears and anxieties. As most of us know, there have been a number of major websites that have been hacked in recent years, some instances more widely publicized than others. The ultimate victims are the individuals whose personal data has been breached and compromised. The term “pwned” originated in early online gaming as a typographical error in the word “owned”. If you have been “pwned”, it means that your personal information is now “owned” by others. To see if your personal data has been “pwned”, visit the “Have I Been Pwned?” website and enter your email address. At the time of this writing, there are 296 websites that have been “pwned” with over 5 billion accounts compromised. Some of the websites that have been hacked include Adobe, Ancestry, Avast, Comcast, Dropbox, Exactis, Experian, Forbes, Kickstarter, LinkedIn, MySpace, River City Media, Snapchat, Ticketfly, tumblr, and Yahoo. This list includes websites that you have probably used, and in all likelihood, your personal information has almost certainly been hacked. In my own instance, my email address has been compromised in 10 of these major hacks, most recently the Exactis hack in June 2018. That recent hack disclosed credit status information, dates of birth, email addresses, income levels, marital statuses, names, phone numbers, physical addresses, and much more from 340 million personal data records.
Stolen passwords are then readily exchanged, sold, or even made freely available on a number of forums and so-called “pastes”, utilized by cybercriminals who are well aware of the human tendency to reuse usernames (many simply the users’ email addresses themselves) and passwords across a variety of websites. Security breaches like the Yahoo and Dropbox hacks go back to 2012. Although savvy Internet users will have changed their passwords on those sites long since then, if those same passwords were used on other websites, the vulnerability remains. More recent hacks will expose passwords that are currently in use, demonstrating a strong argument in favor of changing passwords on a regular basis.
With this combined background information in mind, you will understand how I felt both alarmed and violated when I received an email one evening back in July that made it past the Gmail spam filter. The subject line included a username and password combination that I frequently used 10 or 15 years ago, indicating that somebody had gained access to my personal information, even though it no longer represented valid credentials. The email had successfully caught my attention and, at first glance, seemed like there could be cause for concern. It went on to allege that a visit to pornographic websites led to the installation of remote access and keyboard logging software on my computer that gave the hacker complete access to my email and social media address lists, as well as my computer’s microphone and camera. Cutting to the chase, the sender was threatening to send a compiled split-screen video of the sites I had visited, along with my “interactions” with those sites, to my friends and family members as allegedly compiled from access to my computer. The only way to prevent this from happening was to pay $3,200.00 in Bitcoin (a cryptocurrency that is popular with online thieves) using a key that was provided.
The facts that I do not spend my time visiting pornographic websites, do not have either a camera or microphone installed on my computer, would immediately know if somebody had remote access to my computer, my passwords are highly secure, and Trend Micro Maximum Security software shows that my computer is free of any malware, spyware or viruses, still left me feeling personally violated. The following morning, I spoke with an agent at the Federal Bureau of Investigation’s Boston field office who told me that this extortion scam had been circulating quite widely throughout the month of July 2018. (In fact, I found a variation in my spam folder a couple days later, with this second thief only seeking $250.00 in Bitcoin.) The agent also told me that there were people who reported receiving variations that were sent through the mail. I also have friends and clients who told me that they have received the same sort of email during the same time period and as recently as last week. I went on to file an online complaint with the FBI’s Internet Crime Complaint Center, commonly referred to as the IC3. There is also a page on the Krebs on Security website that outlines the “Sextortion” scam and currently includes nearly 1,000 comments from people like me who have received the emails and are trying to warn others from falling victim.
The lessons to be learned are to:
- Be aware that your personal information has been stolen, probably on multiple occasions.
- Your personal information can be used in extortion attempts.
- Minimize vulnerabilities on your computer and run up-to-date security software.
- Never trust any email that sets a deadline or seeks payment in cryptocurrency.
- Never make an extortion or ransom payment.
- Notify legal authorities if you are a victim.
It is challenging enough running a small business these days. Nobody needs to waste time, worries, or money with the perpetrators of online scams, who are going to continue to evolve into using more creative and credible formats.
This post was written by Peter Pelland
Tags: bitcoin, cryptocurrency, hacks, online extortion, online scams, passwords, sextortion
Posted in Cyber Security, Scams |
Securing Your Digital Identity
June 25th, 2018
In recent months, I have been taking the “10 Steps for Securing Your Digital Identity” seminar – that I first presented at the National ARVC Outdoor Hospitality Conference & Expo in Raleigh in 2017 – on the road, with presentations before several state association meetings. The information in the seminar, drawing parallels between the 2017 Equifax security breach and the risks that face small businesses like yours and mine, seems to continually grow timelier with each presentation.

Equifax has admitted that more data was compromised than was originally disclosed, the Internal Revenue Service (which cancelled a no-bid contract with Equifax) urged taxpayers to file their returns as early as possible in 2018 because a stolen identity can lead to a stolen tax refund, and Facebook admitted that it profited from personal data that was exploited by Cambridge Analytica for nefarious marketing purposes. That latter instance forced Facebook CEO Mark Zuckerberg to uncomfortably don a suit and tie, and led to the May 1, 2018 announcement by Cambridge Analytica that it was shutting its doors and initiating bankruptcy filings in both the United Kingdom and the United States.
Some people have suggested disconnecting from the Internet and deleting their social media accounts. The former suggestion is highly impractical in today’s interconnected world, and the latter suggestion – perhaps laudable – in unnecessary if some common sense precautions are exercised. Let me share just two of the highlights from my seminar that will help you to secure your digital identity.
Passwords
There is no easier way to ensure that your identity will be compromised than by using weak passwords, the same password for more than one account, or a password that you have not changed since the sun started rising in the East. A weak password is like the old skeleton keys that could open every door in the neighborhood when I was a child. If you think that your password is secure, you can quickly test its strength online at https://howsecureismypassword.net/. You do not want a password that can be cracked in seconds, minutes, days, weeks, months or even years, but a password that would require millions, billions or trillions of years to crack. I recommend tools that generate secure random passwords, such as the one at https://passwordsgenerator.net/, where secure passwords typically consist of a minimum of 16 characters that mix upper and lower case letters, numbers, and special characters.
Another option is to use four totally random and unrelated words in succession, such as kitten, faucet, maple, and magnet: kittenfaucetmaplemagnet. According to the online test, that example would take 277 trillion years to crack. The only problem is that most of us find it difficult to think in such a random manner. However, if you make a conscious effort, you can generate a highly secure password that should be relatively easy to enter into a keypad. The most common complaint even then is that secure passwords are difficult to remember.
The solution is to use one of several available password safes, including LastPass, Dashlane, and Keeper. These all work with Windows, Mac, iOS, and Android operating systems, have plugins for popular browsers, include two-factor authentication, offer fingerprint login on mobile devices, and have free versions which are usually all that you need. You only need to remember one highly secure master password. Even if that master password could somehow be hacked, nobody could log into your account thanks to two-factor authentication. If somebody attempts to log into my own password safe (which has happened more than a dozen times from hackers around the globe), they would have to know my master password (good luck!), then – because they would be logging in from an unrecognized device or IP address – they would also need to steal my phone AND know how to unlock that device in order to enter the two-factor authentication.
Software Updates
The massive Equifax security breach was the result of the company’s failure to install a patch in universally used Apache Struts open-source software in a timely manner. The Apache Foundation discovered a vulnerability in its software on March 7, 2017, announcing and patching that vulnerability the same day and issuing a subsequent patch three days later. Equifax failed to apply those urgent security patches for at least two months, resulting in a hack that compromised virtually every consumer in America, including at least 209,000 credit card numbers. Offering free identity theft protection and credit card monitoring service is a poor substitute for basic responsibility. In the fallout, Equifax’s CEO was forced to resign, its stock value plummeted by over 30% almost overnight (only recovering half of that loss at the time of this writing), it lost that multi-million dollar no-bid contract to provide taxpayer identity services for the IRS, and the company’s name is now almost always followed by the words “security breach.”
What are the lessons to be learned by your small business? First and foremost, it is critical to run the latest operating system and updates on all of your computers and mobile devices. If you are running a Windows computer, this means running the latest version of the Windows 10 operating system. Microsoft’s support for Windows Vista ended on April 10, 2012; support for Windows 7 ended on January 13, 2015; and support for Windows 8/8.1 ended on January 9, 2018. If you are running any of those operating systems, your computer and the files that it contains are at high risk. It is also important to be running the latest version of Internet browsers, such as Chrome, Firefox, Edge, and Safari; plug-in software such as Adobe Reader, Adobe Flash Player, and Java; and a reliable anti-virus software suite from companies like Avast, Trend Micro, Webroot, or Bitdefender.
Hack attacks are continuous and ongoing, seeking out vulnerable passwords and vulnerabilities in software. Without taking basic precautions, you could become the next victim of identity theft, be subjected to ransomware demands, have your credit card information stolen, or compromise the personal information of every one of your customers. The resulting impact could be devastating for your business. The days have long past when any business, large or small, can afford to take anything less than a vigilant stance when it comes to securing its digital identity.
This post was written by Peter Pelland
Tags: Cambridge Analytica, Dashlane, Equifax, Keeper, LastPass, password safes, passwords, secure passwords, software updates
Posted in Cyber Security |
Keep Your Passwords Secure
November 26th, 2017

If you attended my “10 Steps for Securing Your Digital Identity” seminar at the 2017 Outdoor Hospitality Conference & Expo, you learned that my lead segment involved the importance of keeping your passwords secure. Passwords have been around since ancient times, when the first sentry asked “Who goes there?”, becoming essential for admission to a speakeasy during Prohibition, and playing a vital role in military security during World War II.
When I was growing up in the 1960s, the doors to our house had old mortise locks and keys that gave our family a sense of security. I recall that the logic when the doors were locked at night was to keep the key turned 90 degrees in the keyhole on the inside of the lock, under the presumption that this would prevent a thief from inserting a key into the outside of the lock and gaining entry. Of course, if somebody got locked inside, we knew that it would only take a couple of minutes to jimmy the key out of the lock. When we were away from home, the key came with us, leaving the lock even more vulnerable.
If a key got lost or broken, we simply walked to the neighborhood hardware store (yes, they existed back then!) and bought a skeleton key for 50¢ that would probably open every lock in our house, including the outside entry doors, as well as the locks on most every other house in the neighborhood. It is no wonder that we relied on neighbors to keep an eye on our houses back then. Sadly, many people today do not even know the names of their neighbors.
Nowadays, passwords are almost exclusively associated with computers and Internet security, and a lame password is essentially the equivalent of a skeleton key. Like those families sleeping soundly behind the security of a mortise lock, a majority of computer users think that their passwords are securely protecting their accounts from getting hacked.
Before I go any further, I would like you to test one of your passwords. Go to this URL and enter your password: https://howsecureismypassword.net/. As an example, I just tested “JBDayton62”, which is exactly the type of password that many people use, so falsely confident in its security that they use it on every account that requires a password. According to the test, a computer could crack this 10-digit password in only 8 months; however, anybody who researched the Internet and social media and already knew that John Brown was born in Dayton, Ohio in 1962 could crack this password in no time flat. If a password is convenient to remember, it is easy to crack!
What Constitutes a Secure Password?
Quite simply, for a password to be secure it should consist of a minimum of 16 characters; never contain a word or a combination of words found in the dictionary; never contain the names of family members, friends, pets, sports teams, and the like; and be made up of a random combination of uppercase letters, lowercase letters, numbers, and special characters. You can also often use spaces in passwords, although it is unfortunate that many websites still prevent users from choosing truly secure passwords, by precluding the use of special characters, for example.
The next rule is to always use a unique password for each and every site, and then to change each password on a routine and frequent basis. Apply even stricter standards for sites that provide access to highly secure information, such as your online banking or the IRS’s Electronic Federal Tax Payment System (EFTPS) website. The time to change your old, reused, vulnerable, weak, or compromised passwords is now, not next week or “when you get around to it.”
Before you naively presume that nobody is out there trying to crack your password, consider the fact that password cracking software is readily available online for use by hackers (and occasionally by companies that are on the lookout for weak passwords being used by employees.) Those programs include L0phtCrack, Cain, and John the Ripper … all designed to crack passwords (and sometimes credit card numbers) using brute force, dictionary attacks, rainbow tables, and other means.
How to Create a Secure Password
Never trust yourself to generate your own secure password. Our brains are simply not programmed to think randomly, and any password that makes sense to you is easy to crack. Some people even think that including a foreign-language word in their password will make it secure, perhaps presuming that hackers only reference English language dictionaries (even though English may be far from their native languages.) My recommendation is to use a secure online password generator such as the Secure Password Generator: https://passwordsgenerator.net/
The Secure Password Generator will allow you to choose any length of characters (from 6 to 2,048) and choose the types of characters that will be allowed (or excluded, if a site does not permit certain characters), then generate it on your own computer.
How to Store Your Passwords
Once you generate a highly secure password, keeping it written down on a sheet of paper or in a Word document on your computer is like leaving the keys for Fort Knox at a lost and found counter. You need a way to store and access your passwords safely, relatively easily, and securely. I recommend the use of a password safe. Three of the best are LastPass, Dashlane, and Keeper.
LastPass – https://www.lastpass.com/
Dashlane – https://www.dashlane.com/
Keeper – https://keepersecurity.com/
All three work with Windows, Mac, iOS, and Android operating systems; have plugins for popular browsers; include two-factor authentication; include form-filling; offer fingerprint login on mobile devices; and have free versions.
The idea with a password safe is that you have only one highly secure master password to remember. Thanks to geolocation, if you login to your account from an unfamiliar IP address, the two-factor authentication will kick in, requiring you to confirm your identity before being allowed access. In my own instance, 12 attempts to login to my account over the last 6 months have been thwarted – 3 from Vietnam, 2 from China, 2 from Brazil, and one each from Argentina, Georgia, Ukraine, The Philippines, and the United States (North Carolina). Do not think for a moment that there are not people out there actively trying to hack into your accounts. They are out there and they are everywhere.
Access to our personal data is far too important to be left to chance, and I am hoping that this article might help to open the eyes of a few disbelievers. People who are ahead of the curve when it comes to planning are already taking measures to ensure the longevity of access to their data, even as new biometric methods such as fingerprint and iris recognition are coming into play. According to a survey taken by the University of London and cited in Wikipedia, one in ten people are now including password access or recovery information in their wills. My best advice is to think toward the future, but to start changing your way of thinking today.
This post was written by Peter Pelland
Tags: Dashlane, Keeper, LastPass, password security, password storage, passwords, strong passwords
Posted in Cyber Security, Uncategorized |
Passwords: First Line of Defense against Identity Theft
February 14th, 2017
Passwords have come a long way since the days of Prohibition, when a knock on the door of a speakeasy required the necessary password for entry and the consumption of illegal liquor. Today, we use passwords and personal identification numbers for just about everything online, in an effort to protect the privacy of our personal information.
Identity theft has grown rampant, proliferating at a time when almost every personal or business transaction passes through one or more computer network. According to the Federal Trade Commission’s latest annual report (covering the 2015 calendar year, with the 2016 report due out in February 2017), there were 480,000 identity theft complaints filed during that time period. Of these, 45% involved tax- or wage-related fraud, 16% involved credit card fraud, 10% involved phone or utilities fraud, 6% involved bank fraud, and 4% involved loan fraud.
One recent report surmised that 15 million Americans have become the victims of identity theft in 2016. That means that 7% of all adults have been victimized in this year alone, with an approximate per-instance loss of $3,500.00. On average, these people spend an additional $500.00 and 30 hours of time trying to recover their identities and make their private information less vulnerable.
Start with Your E-Mail Passwords
My company provides e-mail hosting services through Google and Rackspace for our website hosting clients, and it is rare for a few days to pass without being contacted by a client who has purchased a new computer or mobile device but has misplaced an e-mail account password. For obvious reasons, we do not store those passwords, and we strongly advise our clients to keep records of their passwords in a secure location. Our only option is to assist with changing the lost password, which will then require that passwords be updated on any other actively used devices.
When setting up those e-mail accounts (or updating a password), clients are often annoyed that we will not agree to use a weak password like 123456, abc123, password, passw0rd, qwerty, steelers, yankees, football, baseball, camaro or firebird. (Yes, those are actual passwords that consistently show up on compiled lists of weak passwords.) In fact, Google’s Gmail will not allow an admin to use a password that is made up of fewer than 8 characters (although there are no further password security requirements beyond this minimum length.)
Some people make an attempt at generating a secure password that they can still remember. For example, they might concoct “AIwfCim2ft” from “All I want for Christmas is my 2 front teeth.” The rule of thumb is to use something that is both easy to remember and difficult to guess. This is definitely a step in the right direction, but something totally random that also uses special characters and spaces would be even better, although far less memorable.
Secure passwords will provide a layer of protection against some bad character obtaining your password and hacking into one of your accounts, but they are of far less value in protecting your identity should your account be one of thousands (or millions) compromised in a major data breach.
Hacks Happen
You do not need to be Sony Pictures getting under the skin of Kim Jong Un. Big companies are routinely targeted by hackers from around the globe, putting the security of their subscribers at risk when a breach occurs. In general, big businesses take extraordinary measures to attempt to maintain the utmost security standards, but it is an ongoing game of cat and mouse. For example, Facebook alone has paid out over $5 million to date in its not-highly-publicized Bug Bounty program, where it pays independent “white hat” hackers to identify and repair security vulnerabilities.
That is an example of what one big online business is doing; however your own personal security is to a great degree your own responsibility. You will want to check (and often disable) routinely loose security settings when you buy a new computer or mobile device or when you upgrade one of those to a new operating system. Keep in mind that settings that benefit convenience and ease of use are very often directly at odds with the safeguarding of your personal security.
There are many ways that passwords can be hacked online. The most common technique is the use of dictionary attacks, where commonly used words are highly vulnerable and easily uncovered. Another technique consists of using the brute force of computing power and sophisticated software to run through every possible combination of characters. The more bits of data involved (directly proportional to the number and random nature of characters), the longer it will take to hack a password. Complex character combinations and the use of encryption slow down, but will not prevent, the disclosure of a password to a determined intruder.
There are actually times when a company or individual needs to recover a lost password, and there are other instances where law enforcement needs to crack a password in order to uncover criminal activity. We are all familiar with the FBI vs. Apple Computer encryption debate, involving a cell phone owned one of the shooters in the December 2015 San Bernardino, California terrorist attack. Whether used for good or bad, there are dozens of free, open-source brute force hacking tools that can be easily found and downloaded online. Their existence and ease of access should provide a wake-up call to any computer or mobile device user.
Just in case you think that one of your own passwords is “secure enough”, enter it into this online tool for what will probably be a rude awakening:
https://howsecureismypassword.net/
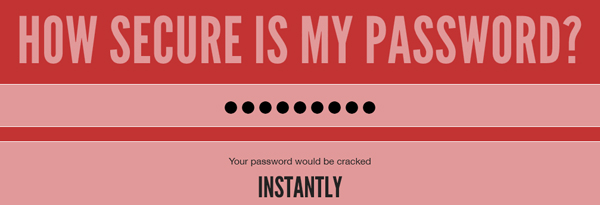
Minimum Standards
The minimum standards for password security that are generally considered acceptable today involve the use of at least 12 (preferably 16) entirely random characters (a mix of upper and lower case letters, numbers, spaces and special characters), never including a dictionary word or a repeated sequence, and with no password used in more than one application.
There are several online tools that will assist you in generating secure random passwords. Using one of these tool, I just generated a random 16-character password that I then entered into the secure password test site (shown above.) According to that site, the password that I entered would take 41 trillion years to crack. Here are two such password generator tools. Give one of them a try:
Password Generator
https://passwords-generator.org/
Bitwarden Password Generator
https://bitwarden.com/password-generator/
Storing Passwords
The best advice for keeping track of your cryptic passwords is to always maintain a written paper record in a very secure location. To simplify your life, you can also use one of several password managers that will allow you to encrypt and store all of your passwords in one secure location. You will only have to remember one password to access your files. (If you have been following along and learning from what I have written, that password will meet the standards that I have outlined above.)
The following are some of the best free password managers. They all work across multiple devices. Compare their features and choose one:
LastPass • Dashlane • KeePass
Bear in mind that even these password managers are vulnerable to hackers; however, in one documented security breach, only users with weak passwords were impacted. We are over a month into a New Year. Resolve to at least take a step in a positive direction when it comes to your online security.
This post was written by Peter Pelland
Tags: computer hacking, cyber security, e-mail, identity theft, passwords, strong passwords
Posted in Cyber Security |
|



