Keep Yourself Safe, Keep Us All Safe
October 4th, 2023
You may recall news reports in early June 2023, regarding the hack of the MOVEit file transfer software by a ransomware extortion group based in Russia, known as “Cl0p” but more commonly referred to as “Clop”. Keeping in mind that the vast majority of ransomware instances are not publicly reported, in order to avoid both embarrassment of the victims and attention for the perpetrators, this one was disclosed for a number of reasons. For one, it was widespread, affecting a diverse group of victims that included the U.S. Department of Energy and other federal agencies, Johns Hopkins University and the Johns Hopkins Health System, the University System of Georgia, CalPERS (the California Public Employees’ Retirement System), the Province of Nova Scotia, Shell Oil, British Airways, the BBC, and the state motor vehicle departments in Oregon and Louisiana. A second reason was that Clop publicized the victims of its exploit on the dark web. Whether or not you had ever previously heard of MOVEit, software that is widely used by companies and organizations around the world to share sensitive data, you may very well have used similar file transfer products such as WeTransfer and Dropbox.
In the MOVEit instance, the hackers exploited a previously unknown vulnerability in the software, gaining access to users’ files before the software could be patched. This is what is referred to as a zero-day exploit, when software engineers have “0” days to patch a vulnerability prior to its exploitation. What made this extortion a bit atypical was the fact that the perpetrators did not follow the usual pattern of locking down victims’ computers until a ransom was paid, but instead threatening to release sensitive data that had been accessed unless their ransom was paid, as always, in the form of Bitcoin or another cryptocurrency. According to the latest information published by Palo Alto Networks, which monitors ransomware payment trends, the average ransom demand rose to $2.2 million in 2021, with the average payment rising to $541,010.
The Value of Your Personal Data
Ransoms are one thing, but the stolen data may be even more profitable when sold on the dark web. Let’s very conservatively presume that a hack discloses the private data of 5 million users. According to Privacy Affairs, an organization that monitors and compiles lists of prices for personal information when sold online, the following are just a few examples of the going prices for everything from social media logins to credit card accounts.
- Credit card details, account balance up to $5,000: $110
- Credit card details, account balance up to $1,000: $70
- Stolen online banking logins, with a minimum balance of $2000 on account: $60
- Stolen online banking logins, with a minimum balance of $100 on account: $40
- Cloned Visa, MasterCard or American Express account with PIN: $20
- USA hacked credit card details with CVV: $15
- 50 Hacked PayPal account logins: $120
- Hacked Gmail account: $60
- Hacked Facebook or Instagram account: $25
- Hacked Twitter account: $20
- US eBay account: $20
- Netflix account, 1-year subscription: $20
- Hacked Spotify account: $10
- 10 million USA email addresses: $120
Clearly, these international thieves are playing a numbers game. Although the hackers in the MOVEit incident exploited a software vulnerability, the majority of breaches occur as the result of human error. Most typically, those errors involve unwarily responding to a phishing scam, carelessly clicking on a link, or using the same (usually weak) password on multiple sites. Many phishing scams appear legitimate because they utilize data from earlier corporate hacks. For example, if an email service provider has been hacked, its subscriber list will have been compromised, leading to subscribers receiving suspicious emails. Because nobody wants their email service to be disrupted, many people will quickly comply with a request to divulge further personal information.
One of my clients recently received an email, indicating that his email account had been compromised, requiring him to click on a link to confirm his username and password. He did so, without a second thought, then had his email account disabled two days later because it was being used to send out massive amounts of spam, effectively turning his computer into a zombie device. When his password was reset and his account access restored, he received another email, no doubt from the same perpetrators who had lost access to his account, asking him to click on a highly suspicious link in order to “cancel the requested deactivation” of his account. Clearly, they were hoping that lightning would strike the same victim twice. Now you can see why a single hacked Gmail account sells for $60 on the dark web!
Take Precautionary Measures
I have said it before, and let me say it again, that we all need to be highly vigilant before clicking on links in an unsolicited email. If that email contains spelling mistakes or grammatical errors, you can be assured that it did not originate from the company whose graphics have been “borrowed” in order to enhance credibility. Hover over any links, and you will see how they go to some highly suspicious URLs. In addition, take the time to set up and utilize multi-factor authentication on every online account that involves either payments or passwords. Then be sure that you always use a secure and unique password for each site. Many of us tend to “recycle” our passwords, a truly lazy habit. In those instances, a hacked password on one account could lead to hacked access to multiple accounts, falling victim to what is referred to as a “stuffing” attack.
If you would like to learn more about the very serious nature of these online threats, I highly recommend a reading of “This Is How They Tell Me the World Ends: The Cyberweapons Arms Race” by Nicole Perlroth, a cybersecurity journalist for The New York Times and an advisor to the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA). This is a difficult book to put down (so you may want the audio book version), and it will keep you awake at night.
This post was written by Peter Pelland
Tags: cyber security, hackers, multi-factor authentication, personal data, personal privacy, phishing scams, ransomware
Posted in Cyber Security, Uncategorized |
The Latest Scams: Be Alert, Don’t Get Hurt
January 20th, 2023
Sometimes I think that the
Internet was invented by P.T. Barnum, the circus promoter and showman from New
Haven, Connecticut. A century and a half after his heyday, modern-day hucksters
seem intent on capitalizing upon the phrase “there’s a sucker born every
minute” that is commonly attributed to the great Barnum. So-called phishing
scams arriving via email are becoming more prevalent than ever. Phishing is an
attempt to steal personal information or hack online accounts through the use
of deception. Some are easy to spot, while others are more sophisticated in
appearance and subsequently more difficult to detect. The people behind these
schemes prey upon our fears and try to convey a sense of urgency to their bogus
messages. My main words of advice are to step back, take a deep breath, and
avoid the urge to panic.
Learn to detect
and comfortably ignore the lion’s share of these scams by using an effective
spam blocker on your email accounts. When a few slip past the filters and
appear in your inbox, take a close look. Learn to hover and not to click. Is
the actual sending address what it appears to be? One of the latest phishing
scams to be making the rounds is the “Best Buy / Geek Squad Service Renewal”
invoice. I will refer to three specific emails below, all alleging to be sent
from Geek Squad (or in one instance “Geeks Squad Inc.). The first came from edfg0823@gmail.com,
the second indicated that it came from messenger@messaging.squareup.com (and
included an option for payment through Square), with a 160-character cryptic reply-to
address, and the third came from dayaguena@gmail.com.
Although it is easy
to attach any corporate logo to an email, in an effort to make the message
appear to be authentic, would that familiar company really send out a message
with spelling mistakes and sloppy formatting? Just because a message implies
that your bank account, credit card, or PayPal account has been charged for a
product or service that you never ordered does NOT mean that the sender
actually has access to your account. What they are generally hoping is that you
will fall for their scheme, want that alleged charge to be reversed, and
unwittingly provide them with your account information in order to confirm the
“refund”. By doing so, you will have then provided the scammer with the means
to run up fraudulent charges on your account far in excess of the bogus charge
that caught your attention.
The perpetrators
behind the “Best Buy / Geek Squad Service Renewal” scams could possibly have
access to Best Buy customer emails harvested during a 2017 data breach that
exploited a vulnerability in the company’s online chat software; however, it is
more likely that the senders use random email accounts under the presumption
that a significant percentage of recipients will be recent or past Best Buy
customers. (They could also be pretending to represent Walmart, Costco, Target,
or any other well-known brand with an extensive customer base.) I have received
several of these emails recently. One lists an “Order ID”, “Product Code”, and
renewal fee of $417.00 that is ready to be charged to my account, telling me
that “YOUR SERVICE HAS BEEN RENEWED”. The email (which consisted of a JPEG
image) also reads, “According to our contact with you. Your plan will be auto
renewed with in 24hrs and you will be charged $417.00”. The punctuation errors
alone in that message should raise several red flags. Of course, they are
hoping that I will call the “Customer Support Team” using the toll-free number
included.
Another alleged
“Geek Squad Subscription Renewal” was convincingly professional in its
appearance, including a PDF invoice for a “Geek Squad Advanced Protection –
Annual Plan” renewal at $229.99. It claimed that my “account” had just been
charged, and included a toll-free number to call “if you want to cancel the
Renewal and claim the refund.” The telltale signs on this invoice were the
salutation of “Dear Dear”, my name listed as “Dear Customer”, and a random
return address that is a residential home in Mississippi according to Google
Maps. A third email followed the same modus operandi, had my name as “Existing
User”, a random return address in a residential neighborhood of Brooklyn, and
an alleged renewal fee of $299.87 for 3 years and up to 5 devices (the best
deal yet.) It, of course, included a toll-free phone number “in case you wish
to stop this transaction or stop auto-renewal”.
In the first two
of these three instances, the toll-free numbers (which I called from a
randomized phone number) were already disabled. The perpetrators hope that
recipients will panic and call them immediately while their temporary phone
numbers are still enabled. The third number was busy with other callers and
asked me to leave a return phone number. Of course, they will then ask for a
credit card or other account number in order to process the alleged “refund”.
Fight Back!
First of all,
pay close attention to unsafe content warnings in your email software. Then
never respond to requests for your private information, beware of messages that
convey a sense of urgency, and never click on unknown links. If you are one of
the millions of people who use Gmail as your email service provider, you can
report a phishing email that may have made its way to the inbox on your
computer by opening the message, clicking on the three vertical dots next to
the “Reply” icon, then clicking on “Report phishing.” If a phishing email asks
you to make a payment via PayPal, forward the entire email to phishing@paypal.com.
You may also
forward phishing emails to the Anti-Phishing Working Group at reportphishing@apwg.org. This organization includes ISPs, banks, online security
companies, and law enforcement agencies. You can also report phishing attempts
to the Federal Trade Commission at https://reportfraud.ftc.gov/. In the event that you have actually been a victim of a phishing
scam, first contact your bank or credit card company, where you will probably
want to change passwords and cancel your credit card. Then file a report with
the FBI’s Internet Crime Complaint Center (IC3) at https://www.ic3.gov/. In most instances, you may also file a complaint with the office
of your state attorney general.
Nobody
likes being a victim of what is essentially online crime, but it is good to
know how to protect yourself and how to take responsive measures when
necessary.
This post was written by Peter Pelland
Tags: phishing scams
Posted in Cyber Security, Scams |
It’s Never Too Late to Start Guarding Your Privacy
May 10th, 2017
I logged onto Facebook this morning, and I was immediately presented with a sponsored display ad hawking a t-shirt design that read, “Never underestimate an Old Man who listens to Neil Young and was born in September.” If I was naïve, I would see that ad and think, “Wow! This is my perfect t-shirt”, then order one. In the short time in which this ad has been displayed, it has been “liked” by 480 people, shared by 182 people (multiplying its reach at no charge to the advertiser), and has received 61 comments. Every one of those comments is from a man who confirms that he was born in September (usually adding a year from the 1950’s or 1960’s) and wants one of the shirts.
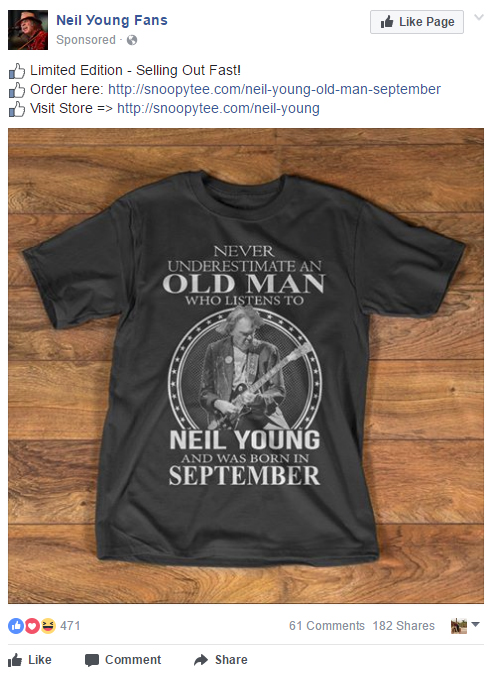
Is the fact that I was shown this advertising a coincidence? No way! It is custom-tailored to my identity. If I went to the order page and modified the URL, I could display any of a number of t-shirt designs based upon:
- The name of the performer.
- The birth month.
- Whether I was a man or a woman.
Here is an example:

To make the ad even more effective, the ordering page includes a countdown clock to create a false sense of urgency:
Depending upon how you view it, being presented these ads is either a brilliant use of Facebook’s marketing potential or an egregious violation of the personal privacy of Facebook users. In this case, I was being shown advertising that was based upon the disclosure of my gender, age, month of birth, and taste in music … all information that I had either voluntarily or unwittingly published on Facebook for either my friends or the world to see.
Yesterday, I was presented with another variation of the ad, based upon the fact that I drive a Jaguar … another fact that I had disclosed on Facebook. Now, I can also order a coffee mug! I am sure that I could modify the URL on the ordering page to change the design to show the name and logo of just about any car company. (On a side note, I have to wonder if these performers and companies are being paid royalties by the t-shirt company for use of their trademarks.)
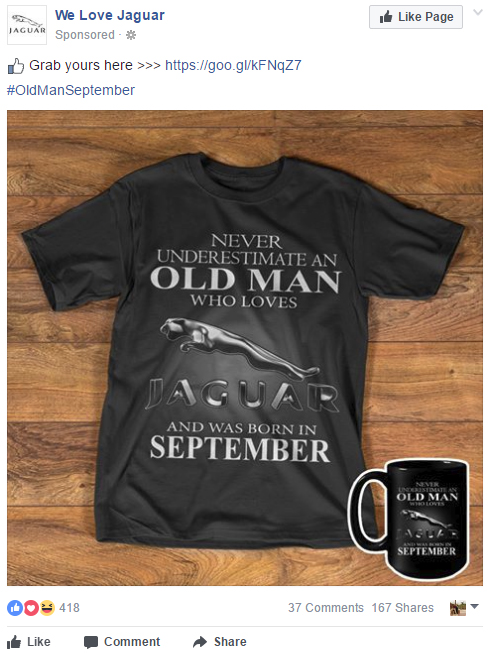
You may think that this is all innocent, fun, and the price we pay for the otherwise free use of social media apps like Facebook, but there is more involved. I don’t know how many times I have seen friends on Facebook post a complete set of answers to 50 personal questions such as the name of their elementary school, their first phone number, name of their eldest sibling, and so forth. Whenever I see this being treated as a harmless and fun exercise, I cannot help but ask myself, “Are you insane?” If any of these questions and answers seems familiar, it is because they are among the same ones that are used as security tests on your online banking or an e-commerce site when you reset a password. Yes, the name of your first pet can lead to the theft of your identity!
You may have seen the recent news about the “Google Docs” phishing scam that proliferated in e-mails on May 4, 2017, said to be the most effective e-mail worm since the “I Love You” virus that caused havoc back in 2000. The scam was effective because it looked legitimate (it is so easy to copy the appearance of a legitimate website!), came from somebody you knew (rather than some random name chosen by a hacker in Belarus), and was spread through the type of shared online document that we have come to accept as routine. Even cautious recipients who would never open an e-mail attachment from a stranger thought that it was safe to download the same sort of document that appeared to have been shared via a cloud service by a known sender. All of these scams, whether relatively harmless or downright nefarious, play upon the human willingness to trust those with access to our personal information.
At the moment, leading into Mother’s Day 2017, there are several gift card scams that are proliferating on Facebook almost faster than they can be identified and taken down. One purports to offer a $50.00 coupon for use at Lowe’s home improvement stores in exchange for taking a short survey, in which you will be disclosing a wealth of personal information. Another purports to offer a $75.00 coupon to Bed Bath & Beyond, the same sort of scam that attempts to gather your personal information for exploitation later.
As I have said in the title of this article, it is never too late to start guarding your privacy. In fact, today is the best day to begin!
This post was written by Peter Pelland
Tags: Facebook Advertising, Facebook scams, identify theft, online scams, phishing scams
Posted in Consumer Trends, Cyber Security, Facebook Tips, Scams |
|




