Beware the “Sextortion” Scam: A New Form of Cybercrime Making the Rounds
October 28th, 2018
Most people realize that the ultimate in cyberwarfare would be for one country to take down the power grid, telecommunications network, financial industry, or military and defense networks of a foe country. There is no doubt that the United States, Russia, China and other countries maintain this capability but wisely withhold use of this “nuclear option” in cyberwarfare, although there have been instances where the waters have clearly been tested. As has been recently demonstrated, cyberwarfare tends to take a much more subtle and individualized approach, exploiting weaknesses in things like social networks and ballot tabulations. The same sort of approach, where individuals are targeted, is generally practiced in cybercrime, the aggressive bully that is the awkward little stepbrother of cyberwarfare.
Cybercrime takes a variety of forms but generally targets either individuals or individual companies. Small businesses, where there is often only a subtle distinction between a business and its owners, can be particularly vulnerable. In most instances, the criminal activity exploits vulnerabilities in the security practices of the target. These vulnerabilities include the failure to apply software patches and updates, unsecure office practices, and the use of weak, old, and/or repetitive passwords. The results include the easy entry of computer viruses and malware that can turn a computer into a bot on a criminal network or install ransomware that will hold a computer and its files hostage. The same vulnerabilities lead to the proliferation of phishing attempts and other email and telephone scams where the senders or callers impersonate trusted companies in an attempt to obtain passwords, secure information like social security numbers, your credit card numbers, or remote access to your computer.
One of the latest trends in cybercrime exploits a combination of known hacks and personal fears and anxieties. As most of us know, there have been a number of major websites that have been hacked in recent years, some instances more widely publicized than others. The ultimate victims are the individuals whose personal data has been breached and compromised. The term “pwned” originated in early online gaming as a typographical error in the word “owned”. If you have been “pwned”, it means that your personal information is now “owned” by others. To see if your personal data has been “pwned”, visit the “Have I Been Pwned?” website and enter your email address. At the time of this writing, there are 296 websites that have been “pwned” with over 5 billion accounts compromised. Some of the websites that have been hacked include Adobe, Ancestry, Avast, Comcast, Dropbox, Exactis, Experian, Forbes, Kickstarter, LinkedIn, MySpace, River City Media, Snapchat, Ticketfly, tumblr, and Yahoo. This list includes websites that you have probably used, and in all likelihood, your personal information has almost certainly been hacked. In my own instance, my email address has been compromised in 10 of these major hacks, most recently the Exactis hack in June 2018. That recent hack disclosed credit status information, dates of birth, email addresses, income levels, marital statuses, names, phone numbers, physical addresses, and much more from 340 million personal data records.
Stolen passwords are then readily exchanged, sold, or even made freely available on a number of forums and so-called “pastes”, utilized by cybercriminals who are well aware of the human tendency to reuse usernames (many simply the users’ email addresses themselves) and passwords across a variety of websites. Security breaches like the Yahoo and Dropbox hacks go back to 2012. Although savvy Internet users will have changed their passwords on those sites long since then, if those same passwords were used on other websites, the vulnerability remains. More recent hacks will expose passwords that are currently in use, demonstrating a strong argument in favor of changing passwords on a regular basis.
With this combined background information in mind, you will understand how I felt both alarmed and violated when I received an email one evening back in July that made it past the Gmail spam filter. The subject line included a username and password combination that I frequently used 10 or 15 years ago, indicating that somebody had gained access to my personal information, even though it no longer represented valid credentials. The email had successfully caught my attention and, at first glance, seemed like there could be cause for concern. It went on to allege that a visit to pornographic websites led to the installation of remote access and keyboard logging software on my computer that gave the hacker complete access to my email and social media address lists, as well as my computer’s microphone and camera. Cutting to the chase, the sender was threatening to send a compiled split-screen video of the sites I had visited, along with my “interactions” with those sites, to my friends and family members as allegedly compiled from access to my computer. The only way to prevent this from happening was to pay $3,200.00 in Bitcoin (a cryptocurrency that is popular with online thieves) using a key that was provided.
The facts that I do not spend my time visiting pornographic websites, do not have either a camera or microphone installed on my computer, would immediately know if somebody had remote access to my computer, my passwords are highly secure, and Trend Micro Maximum Security software shows that my computer is free of any malware, spyware or viruses, still left me feeling personally violated. The following morning, I spoke with an agent at the Federal Bureau of Investigation’s Boston field office who told me that this extortion scam had been circulating quite widely throughout the month of July 2018. (In fact, I found a variation in my spam folder a couple days later, with this second thief only seeking $250.00 in Bitcoin.) The agent also told me that there were people who reported receiving variations that were sent through the mail. I also have friends and clients who told me that they have received the same sort of email during the same time period and as recently as last week. I went on to file an online complaint with the FBI’s Internet Crime Complaint Center, commonly referred to as the IC3. There is also a page on the Krebs on Security website that outlines the “Sextortion” scam and currently includes nearly 1,000 comments from people like me who have received the emails and are trying to warn others from falling victim.
The lessons to be learned are to:
- Be aware that your personal information has been stolen, probably on multiple occasions.
- Your personal information can be used in extortion attempts.
- Minimize vulnerabilities on your computer and run up-to-date security software.
- Never trust any email that sets a deadline or seeks payment in cryptocurrency.
- Never make an extortion or ransom payment.
- Notify legal authorities if you are a victim.
It is challenging enough running a small business these days. Nobody needs to waste time, worries, or money with the perpetrators of online scams, who are going to continue to evolve into using more creative and credible formats.
This post was written by Peter Pelland
Tags: bitcoin, cryptocurrency, hacks, online extortion, online scams, passwords, sextortion
Posted in Cyber Security, Scams |
It’s Never Too Late to Start Guarding Your Privacy
May 10th, 2017
I logged onto Facebook this morning, and I was immediately presented with a sponsored display ad hawking a t-shirt design that read, “Never underestimate an Old Man who listens to Neil Young and was born in September.” If I was naïve, I would see that ad and think, “Wow! This is my perfect t-shirt”, then order one. In the short time in which this ad has been displayed, it has been “liked” by 480 people, shared by 182 people (multiplying its reach at no charge to the advertiser), and has received 61 comments. Every one of those comments is from a man who confirms that he was born in September (usually adding a year from the 1950’s or 1960’s) and wants one of the shirts.
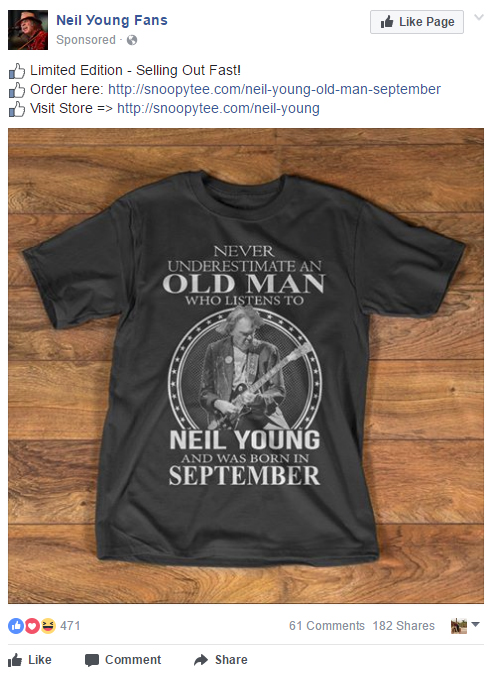
Is the fact that I was shown this advertising a coincidence? No way! It is custom-tailored to my identity. If I went to the order page and modified the URL, I could display any of a number of t-shirt designs based upon:
- The name of the performer.
- The birth month.
- Whether I was a man or a woman.
Here is an example:

To make the ad even more effective, the ordering page includes a countdown clock to create a false sense of urgency:
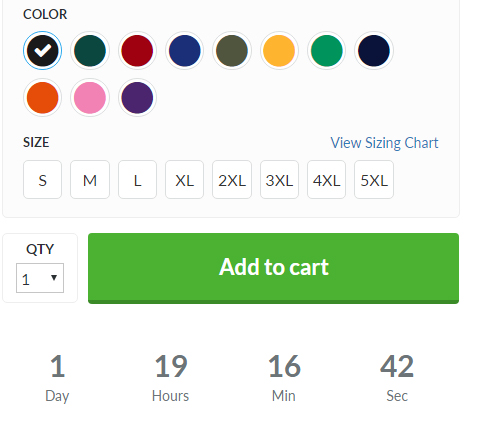
Depending upon how you view it, being presented these ads is either a brilliant use of Facebook’s marketing potential or an egregious violation of the personal privacy of Facebook users. In this case, I was being shown advertising that was based upon the disclosure of my gender, age, month of birth, and taste in music … all information that I had either voluntarily or unwittingly published on Facebook for either my friends or the world to see.
Yesterday, I was presented with another variation of the ad, based upon the fact that I drive a Jaguar … another fact that I had disclosed on Facebook. Now, I can also order a coffee mug! I am sure that I could modify the URL on the ordering page to change the design to show the name and logo of just about any car company. (On a side note, I have to wonder if these performers and companies are being paid royalties by the t-shirt company for use of their trademarks.)
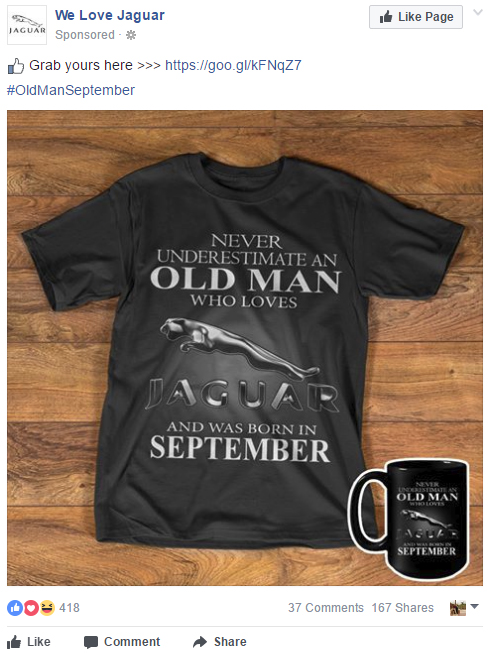
You may think that this is all innocent, fun, and the price we pay for the otherwise free use of social media apps like Facebook, but there is more involved. I don’t know how many times I have seen friends on Facebook post a complete set of answers to 50 personal questions such as the name of their elementary school, their first phone number, name of their eldest sibling, and so forth. Whenever I see this being treated as a harmless and fun exercise, I cannot help but ask myself, “Are you insane?” If any of these questions and answers seems familiar, it is because they are among the same ones that are used as security tests on your online banking or an e-commerce site when you reset a password. Yes, the name of your first pet can lead to the theft of your identity!
You may have seen the recent news about the “Google Docs” phishing scam that proliferated in e-mails on May 4, 2017, said to be the most effective e-mail worm since the “I Love You” virus that caused havoc back in 2000. The scam was effective because it looked legitimate (it is so easy to copy the appearance of a legitimate website!), came from somebody you knew (rather than some random name chosen by a hacker in Belarus), and was spread through the type of shared online document that we have come to accept as routine. Even cautious recipients who would never open an e-mail attachment from a stranger thought that it was safe to download the same sort of document that appeared to have been shared via a cloud service by a known sender. All of these scams, whether relatively harmless or downright nefarious, play upon the human willingness to trust those with access to our personal information.
At the moment, leading into Mother’s Day 2017, there are several gift card scams that are proliferating on Facebook almost faster than they can be identified and taken down. One purports to offer a $50.00 coupon for use at Lowe’s home improvement stores in exchange for taking a short survey, in which you will be disclosing a wealth of personal information. Another purports to offer a $75.00 coupon to Bed Bath & Beyond, the same sort of scam that attempts to gather your personal information for exploitation later.
As I have said in the title of this article, it is never too late to start guarding your privacy. In fact, today is the best day to begin!
This post was written by Peter Pelland
Tags: Facebook Advertising, Facebook scams, identify theft, online scams, phishing scams
Posted in Consumer Trends, Cyber Security, Facebook Tips, Scams |
Beware of Some of the Latest Scams
August 17th, 2015
I always try to do my best to warn readers to avoid getting entrapped by any of the wide range of scams that are prevalent today. We read about them in the newspaper and hear about them on the TV news, but most of us think that they could “never happen to me”, that they only victimize the elderly or people of lesser intelligence. Guess what? Scam operators are good at what they do, and they are getting better all the time.
The way that scams succeed is by being as believable as possible. People fall for the house rentals on Craigslist because the houses are actually there at the addresses listed. They are simply not available for rent, and they are not owned by the crooks who want to collect the first and last months’ rent and security deposits. As people become more aware of the scams, the scammers do a bit more research and become more creative in order to increase their odds of finding their mark.
419 Scams
I recently received a half dozen e-mails from a “woman” who expressed an interest in having a website built, a project that at first glance appeared to be a perfect fit for my company. One of “Jennifer’s” first questions was whether we accepted credit cards. (Had my answer been “no”, I am sure that would have been the end of the e-mails.) The scammer claimed to be based in South Carolina, had an established business importing specialty agricultural products from South America, had a “project consultant” who would be providing us with a logo and text, had a very generous budget, and was very anxious to get the project underway. What was vague was the actual identity of the business and her credentials, other than a fictitious business name.
When my searches for both “Jennifer Mark” and “DW Fresh” came up empty on Google, Manta, LinkedIn, and other online resources, I explained that we would need to review a full credit application and be paid a substantial deposit before any work could commence. Then came the kicker: The scammer offered to roughly double the required deposit, but needed me to do her a “favour” by paying her “project consultant” a $2,800.00 cash payment so that he would release the creative materials while she was “presently in the hospital for surgery”. In other words, I was supposed to accept a $6,500.00 deposit (most assuredly on a stolen credit card), then pay the scammer nearly half of that, with the funds gone from my account before the charge was declined due to the card being identified as stolen.
This type of advance fee fraud is what is generally referred to as a “419 scam”, based upon the section of the Nigerian penal code that addresses fraud schemes. It can involve letters, faxes or e-mails, and – as I have just demonstrated – it has gotten very creative, not necessarily involving extremely large sums of money or trips to Nigeria. What they all have in common is some sort of advance fee. If you run a campground, you could be contacted by somebody who wanted to reserve a block of 100 sites during your off season. That would be welcome income, but curb your excitement unless all of your questions are answered to your satisfaction and there is no suggestion of funds flowing in the opposite direction for any reason.
Officer Ray Fleck
Another scam that has been making the rounds lately has been a robocall from “Officer Ray Fleck”, allegedly working in the audit division of the Internal Revenue Service. I have received these calls. The caller, in a very brash and threatening voice, claims that the Internal Revenue Service is filing suit against you, and that it is imperative that you return the call to make a credit card payment that will satisfy your alleged tax obligations and prevent the filing of suit in your local court. Needless to say, the IRS does not employ a force of thugs who call citizens and demand their credit card numbers, but some people are easily intimidated, making this scam highly successful for its perpetrators.
Windows Service Center
Finally, the “Windows Service Center” scams are still alive and kicking. The callers – usually with heavy accents – claim that they are calling from Microsoft. They are hoping to reach people who have little technical experience and who are coincidentally experiencing some sort of problem with their computers. I received such a call from a person who identified himself as “Jim Sparkle”, and who said that he had been “monitoring my computer” and found that it had a “major problem”. He said that he was “doing his duty” because my computer was “ready to crash down at any time”.
What these scammers want is not only your credit card number but also remote access to your computer, allowing them to install spyware and steal sensitive information. They have various “service plans” that will solve your computer problems, of course suggesting the “lifetime” service plan which was, in my case, discounted to $299.00 and would cover any computer that I ever owned over the course of my lifetime. If you receive one of these calls and have some time to spare, act dumb, and string the caller along a bit (which can admittedly be a bit of fun). You will typically learn at the end of the call that people in other countries have an extensive vocabulary of English language profanities.
The point is that you need to remain vigilant and cautious whenever you are contacted under circumstances that just don’t feel quite right. If you receive an unsolicited contact by anybody who asks you for a credit card number, it is time to end the conversation and continue with business as usual. Scams will always be with us, but with a healthy dose of skepticism, you can prevent yourself from becoming a victim.
This post was written by Peter Pelland
Tags: 419 scams, Jim Sparkle, Nigerian scams, Officer Ray Fleck, online fraud, online scams, telemarketing fraud, telephone scams, Windows Service Center
Posted in Cyber Security, Scams |
|




