It’s Never Too Late to Start Guarding Your Privacy
May 10th, 2017
I logged onto Facebook this morning, and I was immediately presented with a sponsored display ad hawking a t-shirt design that read, “Never underestimate an Old Man who listens to Neil Young and was born in September.” If I was naïve, I would see that ad and think, “Wow! This is my perfect t-shirt”, then order one. In the short time in which this ad has been displayed, it has been “liked” by 480 people, shared by 182 people (multiplying its reach at no charge to the advertiser), and has received 61 comments. Every one of those comments is from a man who confirms that he was born in September (usually adding a year from the 1950’s or 1960’s) and wants one of the shirts.
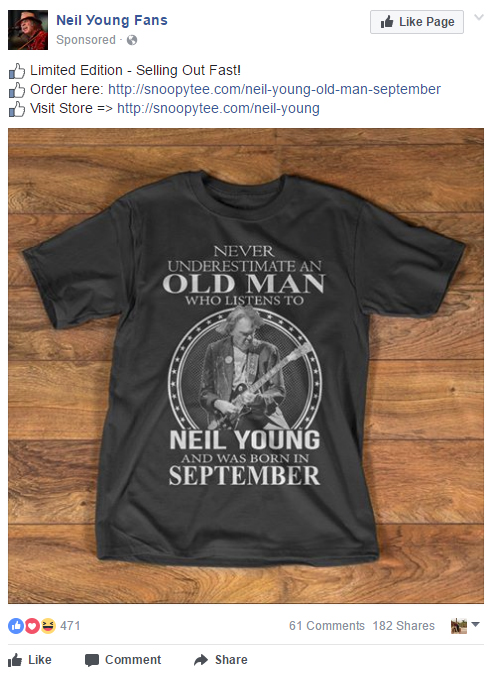
Is the fact that I was shown this advertising a coincidence? No way! It is custom-tailored to my identity. If I went to the order page and modified the URL, I could display any of a number of t-shirt designs based upon:
- The name of the performer.
- The birth month.
- Whether I was a man or a woman.
Here is an example:

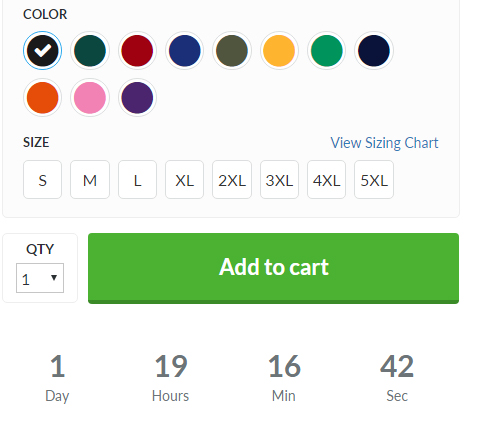
To make the ad even more effective, the ordering page includes a countdown clock to create a false sense of urgency:
Depending upon how you view it, being presented these ads is either a brilliant use of Facebook’s marketing potential or an egregious violation of the personal privacy of Facebook users. In this case, I was being shown advertising that was based upon the disclosure of my gender, age, month of birth, and taste in music … all information that I had either voluntarily or unwittingly published on Facebook for either my friends or the world to see.
Yesterday, I was presented with another variation of the ad, based upon the fact that I drive a Jaguar … another fact that I had disclosed on Facebook. Now, I can also order a coffee mug! I am sure that I could modify the URL on the ordering page to change the design to show the name and logo of just about any car company. (On a side note, I have to wonder if these performers and companies are being paid royalties by the t-shirt company for use of their trademarks.)
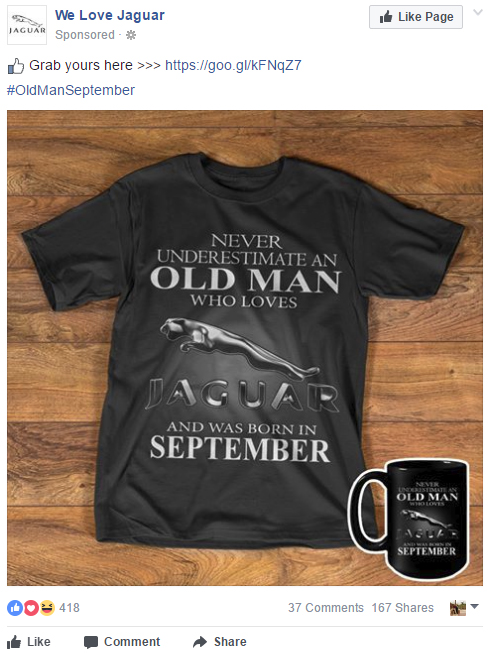
You may think that this is all innocent, fun, and the price we pay for the otherwise free use of social media apps like Facebook, but there is more involved. I don’t know how many times I have seen friends on Facebook post a complete set of answers to 50 personal questions such as the name of their elementary school, their first phone number, name of their eldest sibling, and so forth. Whenever I see this being treated as a harmless and fun exercise, I cannot help but ask myself, “Are you insane?” If any of these questions and answers seems familiar, it is because they are among the same ones that are used as security tests on your online banking or an e-commerce site when you reset a password. Yes, the name of your first pet can lead to the theft of your identity!
You may have seen the recent news about the “Google Docs” phishing scam that proliferated in e-mails on May 4, 2017, said to be the most effective e-mail worm since the “I Love You” virus that caused havoc back in 2000. The scam was effective because it looked legitimate (it is so easy to copy the appearance of a legitimate website!), came from somebody you knew (rather than some random name chosen by a hacker in Belarus), and was spread through the type of shared online document that we have come to accept as routine. Even cautious recipients who would never open an e-mail attachment from a stranger thought that it was safe to download the same sort of document that appeared to have been shared via a cloud service by a known sender. All of these scams, whether relatively harmless or downright nefarious, play upon the human willingness to trust those with access to our personal information.
At the moment, leading into Mother’s Day 2017, there are several gift card scams that are proliferating on Facebook almost faster than they can be identified and taken down. One purports to offer a $50.00 coupon for use at Lowe’s home improvement stores in exchange for taking a short survey, in which you will be disclosing a wealth of personal information. Another purports to offer a $75.00 coupon to Bed Bath & Beyond, the same sort of scam that attempts to gather your personal information for exploitation later.
As I have said in the title of this article, it is never too late to start guarding your privacy. In fact, today is the best day to begin!
This post was written by Peter Pelland
Tags: Facebook Advertising, Facebook scams, identify theft, online scams, phishing scams
Posted in Consumer Trends, Cyber Security, Facebook Tips, Scams |
Passwords: First Line of Defense against Identity Theft
February 14th, 2017
Passwords have come a long way since the days of Prohibition, when a knock on the door of a speakeasy required the necessary password for entry and the consumption of illegal liquor. Today, we use passwords and personal identification numbers for just about everything online, in an effort to protect the privacy of our personal information.
Identity theft has grown rampant, proliferating at a time when almost every personal or business transaction passes through one or more computer network. According to the Federal Trade Commission’s latest annual report (covering the 2015 calendar year, with the 2016 report due out in February 2017), there were 480,000 identity theft complaints filed during that time period. Of these, 45% involved tax- or wage-related fraud, 16% involved credit card fraud, 10% involved phone or utilities fraud, 6% involved bank fraud, and 4% involved loan fraud.
One recent report surmised that 15 million Americans have become the victims of identity theft in 2016. That means that 7% of all adults have been victimized in this year alone, with an approximate per-instance loss of $3,500.00. On average, these people spend an additional $500.00 and 30 hours of time trying to recover their identities and make their private information less vulnerable.
Start with Your E-Mail Passwords
My company provides e-mail hosting services through Google and Rackspace for our website hosting clients, and it is rare for a few days to pass without being contacted by a client who has purchased a new computer or mobile device but has misplaced an e-mail account password. For obvious reasons, we do not store those passwords, and we strongly advise our clients to keep records of their passwords in a secure location. Our only option is to assist with changing the lost password, which will then require that passwords be updated on any other actively used devices.
When setting up those e-mail accounts (or updating a password), clients are often annoyed that we will not agree to use a weak password like 123456, abc123, password, passw0rd, qwerty, steelers, yankees, football, baseball, camaro or firebird. (Yes, those are actual passwords that consistently show up on compiled lists of weak passwords.) In fact, Google’s Gmail will not allow an admin to use a password that is made up of fewer than 8 characters (although there are no further password security requirements beyond this minimum length.)
Some people make an attempt at generating a secure password that they can still remember. For example, they might concoct “AIwfCim2ft” from “All I want for Christmas is my 2 front teeth.” The rule of thumb is to use something that is both easy to remember and difficult to guess. This is definitely a step in the right direction, but something totally random that also uses special characters and spaces would be even better, although far less memorable.
Secure passwords will provide a layer of protection against some bad character obtaining your password and hacking into one of your accounts, but they are of far less value in protecting your identity should your account be one of thousands (or millions) compromised in a major data breach.
Hacks Happen
You do not need to be Sony Pictures getting under the skin of Kim Jong Un. Big companies are routinely targeted by hackers from around the globe, putting the security of their subscribers at risk when a breach occurs. In general, big businesses take extraordinary measures to attempt to maintain the utmost security standards, but it is an ongoing game of cat and mouse. For example, Facebook alone has paid out over $5 million to date in its not-highly-publicized Bug Bounty program, where it pays independent “white hat” hackers to identify and repair security vulnerabilities.
That is an example of what one big online business is doing; however your own personal security is to a great degree your own responsibility. You will want to check (and often disable) routinely loose security settings when you buy a new computer or mobile device or when you upgrade one of those to a new operating system. Keep in mind that settings that benefit convenience and ease of use are very often directly at odds with the safeguarding of your personal security.
There are many ways that passwords can be hacked online. The most common technique is the use of dictionary attacks, where commonly used words are highly vulnerable and easily uncovered. Another technique consists of using the brute force of computing power and sophisticated software to run through every possible combination of characters. The more bits of data involved (directly proportional to the number and random nature of characters), the longer it will take to hack a password. Complex character combinations and the use of encryption slow down, but will not prevent, the disclosure of a password to a determined intruder.
There are actually times when a company or individual needs to recover a lost password, and there are other instances where law enforcement needs to crack a password in order to uncover criminal activity. We are all familiar with the FBI vs. Apple Computer encryption debate, involving a cell phone owned one of the shooters in the December 2015 San Bernardino, California terrorist attack. Whether used for good or bad, there are dozens of free, open-source brute force hacking tools that can be easily found and downloaded online. Their existence and ease of access should provide a wake-up call to any computer or mobile device user.
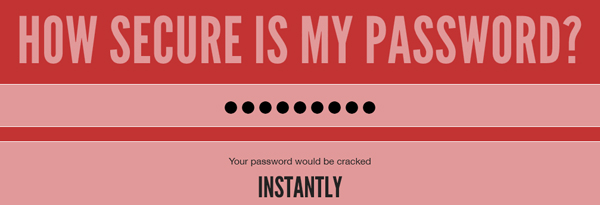
Just in case you think that one of your own passwords is “secure enough”, enter it into this online tool for what will probably be a rude awakening:
https://howsecureismypassword.net/
Minimum Standards
The minimum standards for password security that are generally considered acceptable today involve the use of at least 12 (preferably 16) entirely random characters (a mix of upper and lower case letters, numbers, spaces and special characters), never including a dictionary word or a repeated sequence, and with no password used in more than one application.
There are several online tools that will assist you in generating secure random passwords. Using one of these tool, I just generated a random 16-character password that I then entered into the secure password test site (shown above.) According to that site, the password that I entered would take 41 trillion years to crack. Here are two such password generator tools. Give one of them a try:
Password Generator
https://passwords-generator.org/
Bitwarden Password Generator
https://bitwarden.com/password-generator/
Storing Passwords
The best advice for keeping track of your cryptic passwords is to always maintain a written paper record in a very secure location. To simplify your life, you can also use one of several password managers that will allow you to encrypt and store all of your passwords in one secure location. You will only have to remember one password to access your files. (If you have been following along and learning from what I have written, that password will meet the standards that I have outlined above.)
The following are some of the best free password managers. They all work across multiple devices. Compare their features and choose one:
LastPass • Dashlane • KeePass
Bear in mind that even these password managers are vulnerable to hackers; however, in one documented security breach, only users with weak passwords were impacted. We are over a month into a New Year. Resolve to at least take a step in a positive direction when it comes to your online security.
This post was written by Peter Pelland
Tags: computer hacking, cyber security, e-mail, identity theft, passwords, strong passwords
Posted in Cyber Security |
Nothing Wrong with Accepting Helpful Advice
June 11th, 2016
I think that many of us have become jaded to the thought that somebody might simply be willing to offer helpful advice. We have encountered too many phone calls from telemarketing scam artists, often alleging that they are calling from either Microsoft or Google, when they are really only trying to get their hands on our credit card numbers. It seems unlikely that anyone might be willing to offer assistance without some sort of strings attached. Well, that might not always be the case.
During the course of my work, I frequently encounter websites that are infected with malware or a virus, have forms or other content that are not functioning properly, or are entirely disabled. There are even instances when search results on Google will warn users either that “This site may harm your computer” or “This site may be hacked.”
I encounter these sites most frequently when checking for potential outgoing links – typically area attractions or local tourism districts – to be added to my clients’ websites. I also frequently encounter these warnings attached to do-it-yourself websites, where the webmasters have no knowledge or understanding of server security issues. Google provides several useful resources that will guide webmasters through the recovery process in these instances, but a quick glance will immediately suggest that anyone other than an experienced server administrator will be way out of his league and will be quickly sinking in quicksand.
https://www.google.com/webmasters/hacked/
Malicious content on websites goes hand-in-hand with browser security vulnerabilities, making it all that much more important for computer users to install the latest browser security updates. Between January 26 and April 26, 2016, the Mozilla Foundation has reported 48 security vulnerabilities affecting its Firefox browser – including 15 critical vulnerabilities – that have been patched by security updates … but only if users install those updates. Critical vulnerabilities are defined as vulnerabilities that “can be used to run attacker code and install software, requiring no user interaction beyond normal browsing.” As you can probably deduce, some threats are specific to users of certain browsers, especially outdated versions of those browsers. Sound scary? Absolutely!
https://www.mozilla.org/en-US/security/advisories/
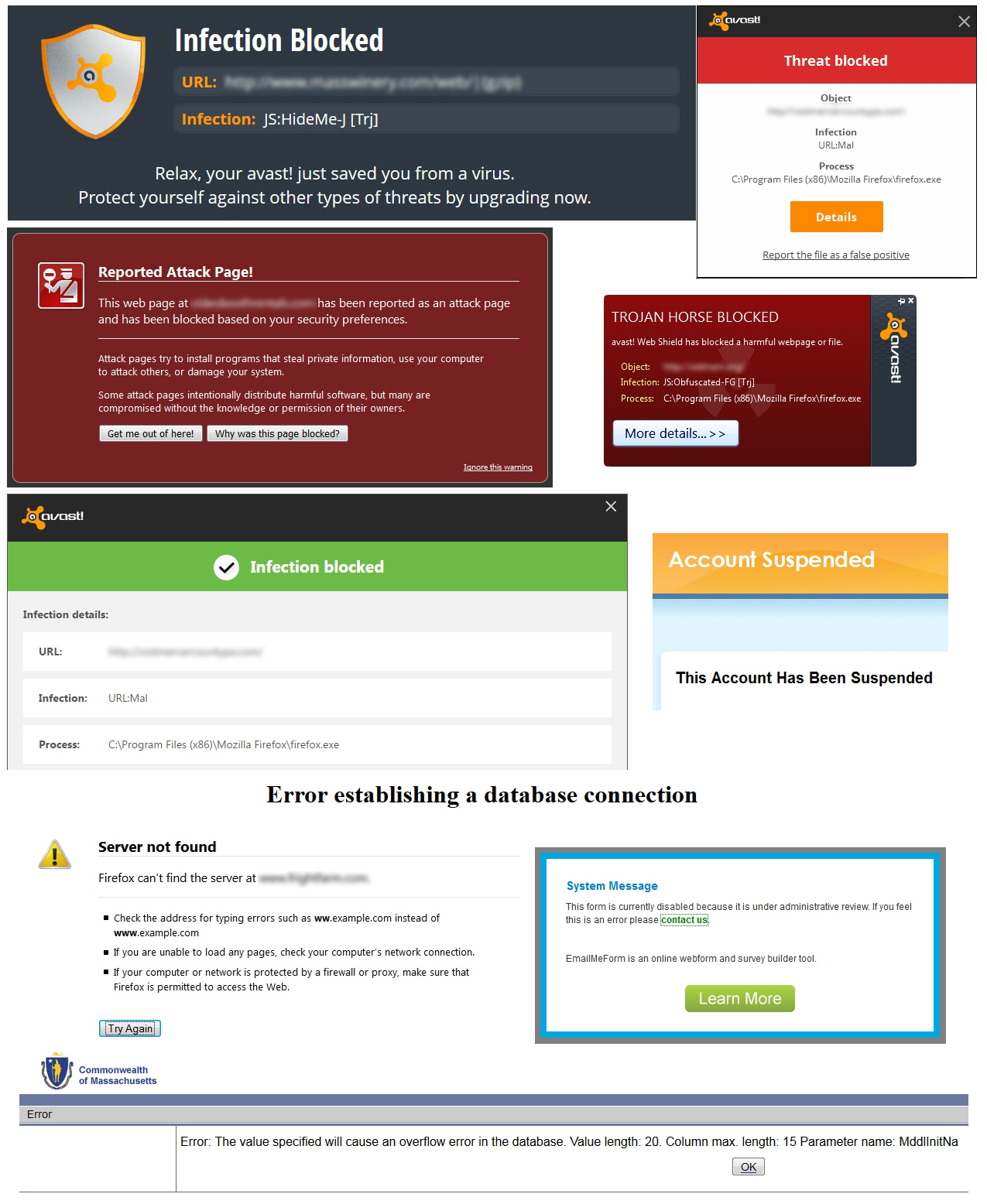
The accompanying graphic shows a collage of just a few of the screen shots of warnings that have been displayed on my computer when clicking through to hacked websites. I have blurred out the website URLs in order to avoid embarrassing the site owners.
I have often called the businesses or associations that own such infected websites, feeling socially responsible to inform them of the problems and explaining that they could be infecting significant numbers of visitors to their sites. In almost every instance, I encounter denial at the other end of the phone, am told that “nobody else has mentioned a problem”, or get brushed off with “we will tell our webmaster” before they hang up the phone. Never once has anybody thanked me for calling a problem to their attention.
If somebody calls you to report a problem with your website, take a moment to listen. Be cautious, if not suspicious, since most of those unsolicited calls are scams; however, at least do yourself the favor of soliciting a second opinion from somebody knowledgeable who you know you can trust.
This post was written by Peter Pelland
Tags: Avast, hacked websites, security advisories, security vulnerabilities
Posted in Cyber Security |
If a Contest on Facebook Sounds Too Good to be True …
September 2nd, 2015
You probably know how that sentence ends. If something sounds too good to be true, it probably is too good to be true. In this case, there have been a number of hoaxes that have circulated on Facebook, and it is amazing how many thousands of people unwittingly think these “contests” are authentic before the pages get reported and eventually get taken down.
Over the weekend, one of my friends on Facebook shared a link and commented how she hoped she would be one of the lucky monthly winners of $5,000.00 in travel money being given away by Qantas Airlines. The page looked very authentic but I immediately detected a scam. The page had relatively few posts for a big corporation, all of which dealt with the contest, and I noticed that it had a total of only 14,190 “likes”. That low number of likes is a dead giveaway that you are not at a legitimate page. A quick search brought me to the real Qantas page, with 715,496 likes and, of course, no such contest.
It turns out that this is not the first time that Qantas has had to deal with the public relations nightmare that can result when people think that a business is somehow responsible for a scam in disguise. In an earlier instance this year, a fake page announced that the airline would be offering free upgrades to first class for all passengers through the end of 2015. That bogus page accumulated some 130,000 likes and over 150,000 shares in the first 24 hours of its existence. Yes, people can be very naïve.
Another friend not long ago shared a link to another Facebook page that captured his excitement. It alleged to be Chevrolet and was encouraging people to enter a contest to win a free Chevy Camaro. I noticed that all of its posts involved the fake contest, most extending the entry deadline in order to get more people to “enter”. Once again, I noticed that the page had relatively few “likes”, and I provided my friend with a link to the real Chevrolet Camaro page on Facebook, not surprisingly with 4,407,269 likes as of this writing. Until somebody reports a page that mimics the identity of a legitimate page and violates its legal trademark, scams like this will perpetuate indefinitely.
One way to quickly confirm the authenticity of a Facebook page is to look for the blue checkmark icon next to the page’s name, confirming that the page of a global brand or business, celebrity or public figure, or media outlet has been verified to be legitimate. Unfortunately, Facebook does not offer this authentication option to small businesses like yours and mine.
If you encounter one of these fake pages, you may be wondering why somebody has taken the time to create it. Typically, the pages are built by individuals who are engaged in the practice of “like farming”, hoping that their page will not be reported and taken down before they will be able to increase its value and profit from it in a black market engaged in the buying and selling of this type of content. Visitors to these pages are usually encouraged to “like” and “share” the pages, whether the incentive is a bogus contest, a chain letter, or simply a photo of a cute puppy or kitten. If a page has more “likes”, it will sell for more money to subsequent scammers who can then engage in more nefarious cons. Many of those are engaged in the collection of personal information that only begins with e-mail addresses and Facebook profiles but could very well end in full scale identity theft.
We all know people who have gotten their personal profiles compromised on Facebook. It can be a nightmare, but for a business, this type of violation can be far more damaging. As a business owner yourself, probably with a Facebook page of its own, you need to be vigilant about protecting your company’s online identity. There can be very real costs in crisis communications and the loss of consumer confidence in your brand. Back in 2012, another airline – Jetstar – suffered tremendous corporate damage when a scammer set up a bogus Facebook page and began posting highly offensive responses to customers posting questions to what they thought was its official page. Instances like this are nothing less than corporate sabotage.
Thinking hypothetically, what would be the direct – and indirect – impact of hundreds or thousands of people being led to believe that you were giving away free merchandise to anybody who showed up at your business next Saturday? It has been sometimes said that all publicity is good publicity, but it does not take much imagination to realize that this adage can be far from true.
Sadly, it is extremely easy to build an official-looking page with very little skill or talent. A con artist copies and pastes a few graphics and trademarks, registers a deceptively similar page name, then posts something that sounds so good to the unwitting that it goes viral faster than it can be taken down. If your business ever finds itself in this unenviable situation, it is imperative that you immediately report the bogus site and that no time is wasted before engaging in damage control and exposing the hoax as broadly as possible.
This post was written by Peter Pelland
Tags: Facebook like farming, Facebook scams, identity theft
Posted in Cyber Security, Scams, Social Media |
7 or 8.1 to 10: Walk, Don’t Run
August 19th, 2015
If you own computers that are running Windows 7 SP1 or Windows 8.1, you are probably aware of the free upgrade to Windows 10 that Microsoft has been rolling out in recent weeks. It all started with a Windows Update that Microsoft released back in April, an “Optional Update” for Windows 7 and a “Recommended Update” for Windows 8.1. That update, as outlined in Knowledge Base Article # 3035583, was solely designed to install the “Get Windows 10” app on your computer, encouraging you to “reserve” your free copy of Windows 10 which would become available after July 29th. That sounded harmless enough, and almost like a “no brainer”, didn’t it?
If you are one of those people who never installs updates, you are certainly putting your computer and your personal data at tremendous risk by not doing so; however, in this instance, none of this will be of concern to you. If you have not seen the “Get Windows 10” icon in the task bar on your computer, simply do NOT install the update that references KB # 3035583.
There are a variety of reasons that some people may not want to immediately upgrade to the new operating system, preferring to upgrade on their own terms and timetable. What most people did not realize when they opted to reserve their copy of Windows 10 was that they would be triggering a 2.7 to 3GB download to take place in the background – potentially hogging bandwidth and slowing down your network performance – for each computer. If you have a cable modem, this should not be a problem, but for anybody with a limited bandwidth allotment or a slow Internet connection, a 2.7GB download could be problematic (and, potentially, a significant expense.) Both the download and the installation are very difficult to stop, but I will provide you with step-by-step instructions below .
With respect to the operating system itself, almost everybody knows that you never want to be among the first people to install new software any more than you want to be one of the first people to buy a new car model that has just rolled off of the assembly line for the first time. It is better to let other people play the role of guinea pigs and test dummies. In the case of Windows 10, released on schedule on July 29th after nearly a year of beta testing, there have already been 3 cumulative updates as of August 14th, all intended to resolve early problems. The cumulative updates combined OS updates and security patches, a recipe that can often lead to unexpected results. Some of the widely identified issues involve video streaming problems when using services like Netflix and YouTube, while other users have reportedly been trapped in reboot loops when installing the updates. A Google search for “problems with Windows 10 upgrade” at the time of this post produces 7,980,000 results.
Perhaps the biggest complaint about Windows 10 is its invasiveness. With the exception of enterprise editions of the software, updates under Windows 10 have all become mandatory, automatically installing whatever software Microsoft wants on your computer, whenever it wants. Independent software developers – much to Microsoft’s displeasure – are already issuing third-party patches that will prevent the automatic updates. More tech-savvy users can already find instructions online that will walk them through the process of disabling some of the more intrusive privacy concerns that are built into the default settings of Windows 10, including settings found in a total of 13 screens under the “Privacy” tab alone.
Microsoft is betting that the vast majority of users will never adjust those settings. To the contrary, my recommendation is that people wait until a wider range of third-party software becomes available that will automate and simplify the process of disabling the many very legitimate privacy concerns involving Windows 10. We all know that the vast majority of people will not take the time to go into settings to make changes – or are simply not comfortable or knowledgeable enough to do so themselves.
There is reason for concern that some of the “features” of Windows 10 are suspected to include a wide range of spyware. Perhaps the most innovative feature of Windows 10 is Cortana, the new conversational virtual assistant that is akin to Apple’s Siri. Cortana’s usefulness is built upon its access to such personal information as your location, calendar, contacts and such. Because Cortana is a conversational tool that has merely been made personalized, it is also constantly listening for your instructions. You may want to weigh the costs versus the usefulness.
People who have read the fine print in the EULA (end user licensing agreement) for Windows 10 find even more reason for concern, reporting that it allows Microsoft to scan your computer to disable any software that it feels is not properly licensed, including software used in various online and cross-device services such as Xbox Live. It also says that Microsoft “will access, disclose and preserve personal data”, including “the content of your emails, other private communications or files in private folders” and “may refer the matter to law enforcement.” The key operative word is not “may”, but “will”.
Just in case you now have second thoughts about installing Windows 10, and you have already “reserved” your copy thanks to unwittingly installing that update, here is how to stop the upgrade from downloading and installing … until you are absolutely sure that you are ready to do so.
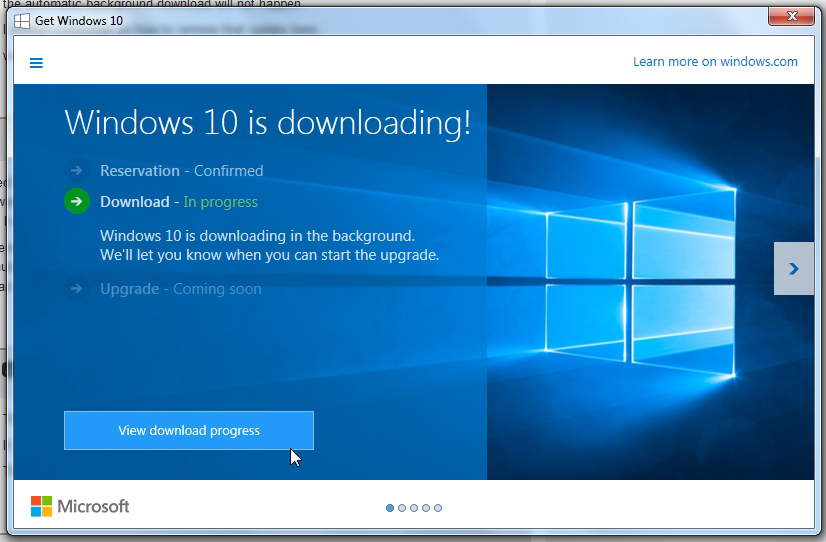
First of all, start Windows Update. You may see that Windows 10 is already downloading. If you see a screen that says “Windows 10 is downloading!” and “Download – In progress”, click on the “View download progress” button. On the next screen, click on the “Stop download” button.
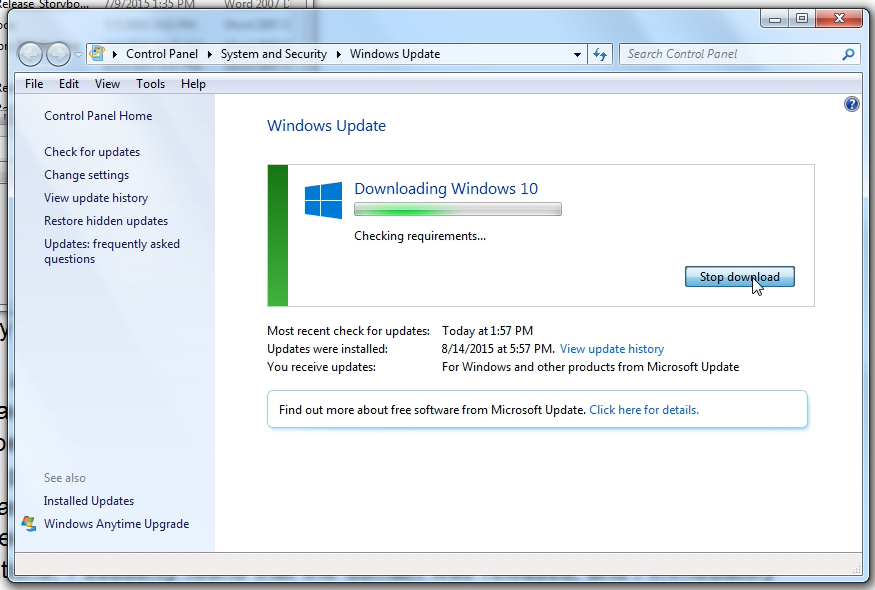
You may also see that Windows 10 has already fully downloaded and is ready to install. If so, do NOT click on the “Get started” button (unless you have decided that everything that I have written is nonsense.)
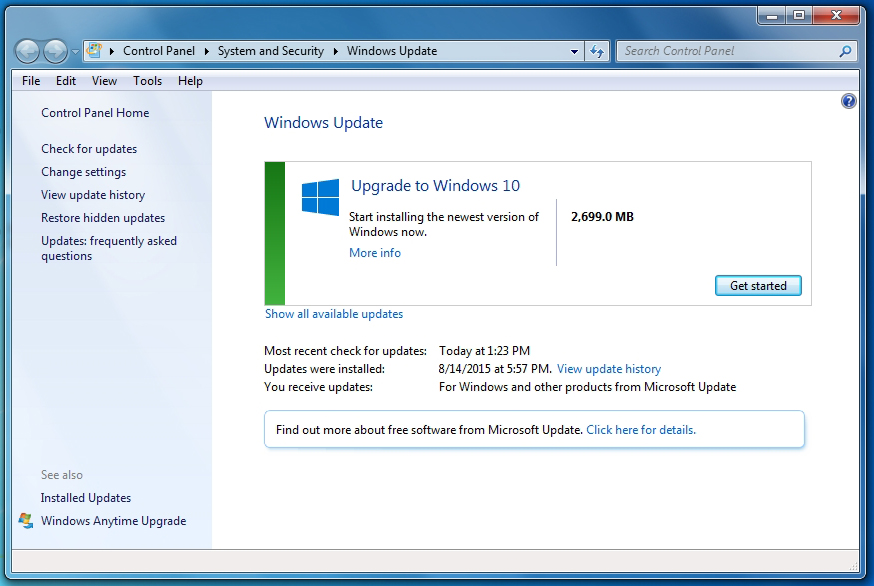
In either instance, click on the “View update history” link on the left of the Windows Update screen, then click on “Installed Updates”. You can use the search box in the upper right corner to look for kb3035583. Click on it in the search results, then choose “Yes” to remove it. You will need to restart your computer (which may take longer than usual.)
When your computer has restarted, go back into Windows Update, and you will see KB3035583 once again appearing as an optional or recommended update. To get Windows Update from nagging you endlessly to re-install the update, right click on it then select “Hide this update”. If Windows 10 has already finished downloading, right click on that as well, then select “Hide this update”. For the moment, you will have taken a few small steps toward maintaining a degree of control of your computer and your personal privacy.
###
Update: August 27, 2015
This morning, it appears that Microsoft will not allow a user to install important updates (in this case, an update to Windows Defender), unless you first allow it to download and install the Get Windows 10 app. The following screen shots show the endless loop that I just encountered when attempting to download and install the important update, without re-installing the update that I do not want.
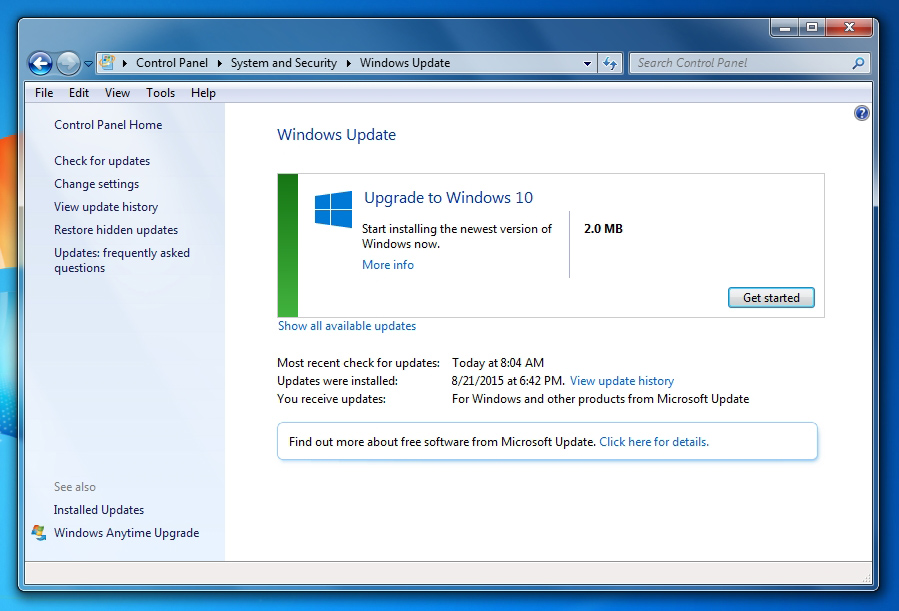
Click on the “Show all available updates” link:
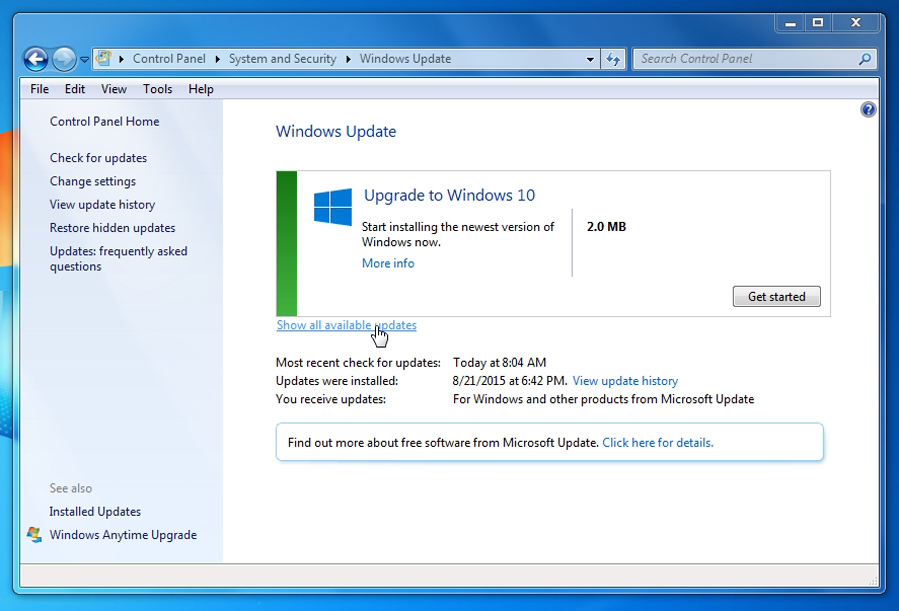
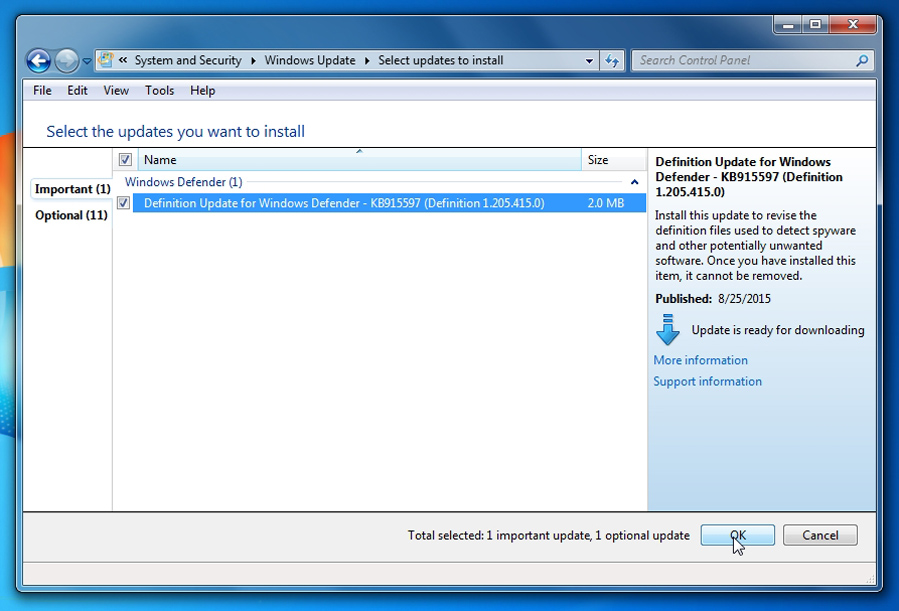
Check the “Important” update that you want to install, then click OK:
Back to where you started, with Microsoft attempting to force you to install the Get Windows 10 app:
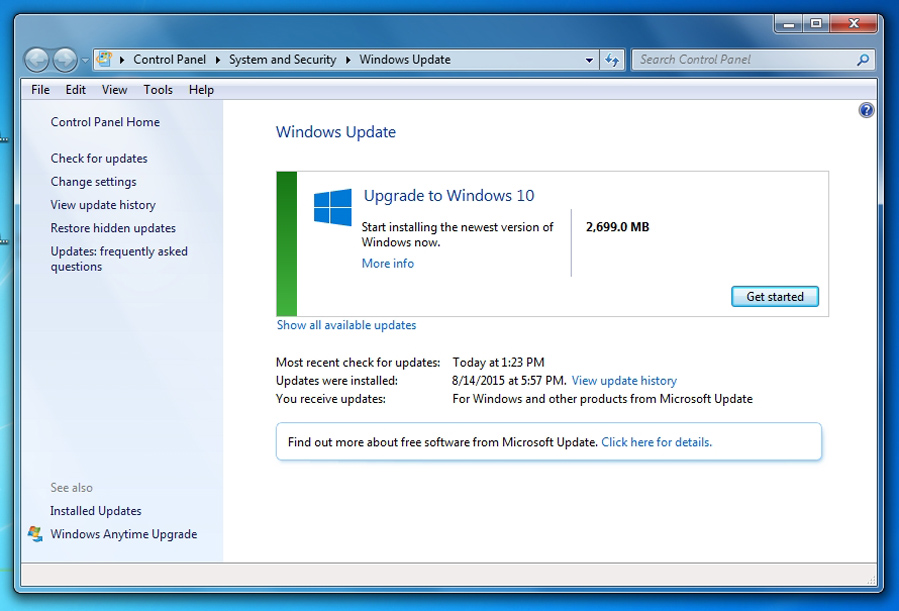
I am sure that there will be more to come. In the meantime, shame on you, Microsoft!
###
Update: August 28, 2015
Here is how to solve the problem outlined above. Click on “Show all available updates”, click to see the Optional updates, then UNCHECK “Upgrade to Windows 10 Pro”.
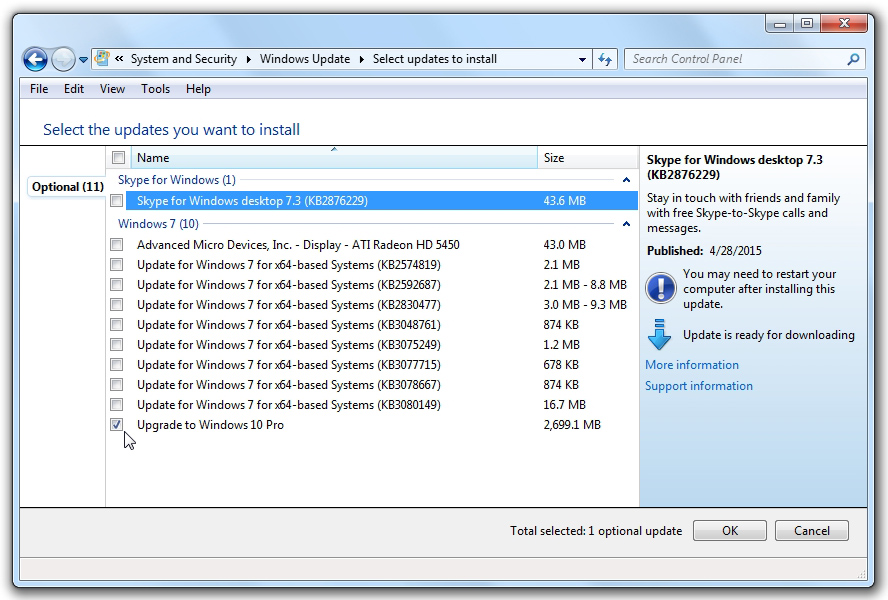
This will allow you to download and install the updates that you want to install, without installing the Get Windows 10 App. You will probably have to do this every time you run Windows Update.
This post was written by Peter Pelland
Posted in Cyber Security |
Beware of Some of the Latest Scams
August 17th, 2015
I always try to do my best to warn readers to avoid getting entrapped by any of the wide range of scams that are prevalent today. We read about them in the newspaper and hear about them on the TV news, but most of us think that they could “never happen to me”, that they only victimize the elderly or people of lesser intelligence. Guess what? Scam operators are good at what they do, and they are getting better all the time.
The way that scams succeed is by being as believable as possible. People fall for the house rentals on Craigslist because the houses are actually there at the addresses listed. They are simply not available for rent, and they are not owned by the crooks who want to collect the first and last months’ rent and security deposits. As people become more aware of the scams, the scammers do a bit more research and become more creative in order to increase their odds of finding their mark.
419 Scams
I recently received a half dozen e-mails from a “woman” who expressed an interest in having a website built, a project that at first glance appeared to be a perfect fit for my company. One of “Jennifer’s” first questions was whether we accepted credit cards. (Had my answer been “no”, I am sure that would have been the end of the e-mails.) The scammer claimed to be based in South Carolina, had an established business importing specialty agricultural products from South America, had a “project consultant” who would be providing us with a logo and text, had a very generous budget, and was very anxious to get the project underway. What was vague was the actual identity of the business and her credentials, other than a fictitious business name.
When my searches for both “Jennifer Mark” and “DW Fresh” came up empty on Google, Manta, LinkedIn, and other online resources, I explained that we would need to review a full credit application and be paid a substantial deposit before any work could commence. Then came the kicker: The scammer offered to roughly double the required deposit, but needed me to do her a “favour” by paying her “project consultant” a $2,800.00 cash payment so that he would release the creative materials while she was “presently in the hospital for surgery”. In other words, I was supposed to accept a $6,500.00 deposit (most assuredly on a stolen credit card), then pay the scammer nearly half of that, with the funds gone from my account before the charge was declined due to the card being identified as stolen.
This type of advance fee fraud is what is generally referred to as a “419 scam”, based upon the section of the Nigerian penal code that addresses fraud schemes. It can involve letters, faxes or e-mails, and – as I have just demonstrated – it has gotten very creative, not necessarily involving extremely large sums of money or trips to Nigeria. What they all have in common is some sort of advance fee. If you run a campground, you could be contacted by somebody who wanted to reserve a block of 100 sites during your off season. That would be welcome income, but curb your excitement unless all of your questions are answered to your satisfaction and there is no suggestion of funds flowing in the opposite direction for any reason.
Officer Ray Fleck
Another scam that has been making the rounds lately has been a robocall from “Officer Ray Fleck”, allegedly working in the audit division of the Internal Revenue Service. I have received these calls. The caller, in a very brash and threatening voice, claims that the Internal Revenue Service is filing suit against you, and that it is imperative that you return the call to make a credit card payment that will satisfy your alleged tax obligations and prevent the filing of suit in your local court. Needless to say, the IRS does not employ a force of thugs who call citizens and demand their credit card numbers, but some people are easily intimidated, making this scam highly successful for its perpetrators.
Windows Service Center
Finally, the “Windows Service Center” scams are still alive and kicking. The callers – usually with heavy accents – claim that they are calling from Microsoft. They are hoping to reach people who have little technical experience and who are coincidentally experiencing some sort of problem with their computers. I received such a call from a person who identified himself as “Jim Sparkle”, and who said that he had been “monitoring my computer” and found that it had a “major problem”. He said that he was “doing his duty” because my computer was “ready to crash down at any time”.
What these scammers want is not only your credit card number but also remote access to your computer, allowing them to install spyware and steal sensitive information. They have various “service plans” that will solve your computer problems, of course suggesting the “lifetime” service plan which was, in my case, discounted to $299.00 and would cover any computer that I ever owned over the course of my lifetime. If you receive one of these calls and have some time to spare, act dumb, and string the caller along a bit (which can admittedly be a bit of fun). You will typically learn at the end of the call that people in other countries have an extensive vocabulary of English language profanities.
The point is that you need to remain vigilant and cautious whenever you are contacted under circumstances that just don’t feel quite right. If you receive an unsolicited contact by anybody who asks you for a credit card number, it is time to end the conversation and continue with business as usual. Scams will always be with us, but with a healthy dose of skepticism, you can prevent yourself from becoming a victim.
This post was written by Peter Pelland
Tags: 419 scams, Jim Sparkle, Nigerian scams, Officer Ray Fleck, online fraud, online scams, telemarketing fraud, telephone scams, Windows Service Center
Posted in Cyber Security, Scams |
Do Not Fall Victim to the Tech Support Phone Scam
March 2nd, 2015
One recent instance after another has compelled me to attempt to warn people about some of the scams that are proliferating and making the rounds these days. Although most scams use e-mail to seek new victims, due to the almost nonexistent cost of e-mail compared to the snail mail that was the vehicle of choice in earlier days, telemarketing is still one of the most common points of entry for scammers and cyber-thieves. In this installment I would like to warn readers about the very active Tech Support Phone Scam, offering suggestions on how to avoid becoming the next victim.
Everybody has problems with their computers from time to time. Files may get corrupted, programs crash, and sometimes a software update contains unanticipated bugs. Worse yet, you could inadvertently install malware on your computer, typically when opening an e-mail or an e-mail attachment. One of my clients recently called me, telling me that he was suddenly experiencing a problem synchronizing Microsoft Outlook with his reservation software. Later that day, he called me again with the “good news” that Microsoft was helping him to resolve the problem. Out of total coincidence, he had been the recipient of a telemarketing call from a dubious outfit that calls itself “Tech Zone Windows”. The caller led my client to believe that he was a Microsoft representative, charged his credit card $199.00 (which was a less expensive alternative to his original $599.00 offer), and was using remote access to do who knows what with my client’s computer! Perhaps the company was actually scanning my client’s computer and removing malware, something that anybody could do themselves for free. Far more likely, it was installing spyware and accessing sensitive information.

Fortunately, the client called me while this was happening, and I instructed him to immediately turn off his computer and found him a legitimate computer technician in his local area. Within seconds, the company’s representative called him, concerned that he had not yet finished the task at hand. My client demanded a refund, but as a result of this experience, has had to take the precaution of replacing his credit card. Hopefully, this represents the end, rather than the beginning, of his problems. Time will tell.
Microsoft has actually warned consumers about this and similar scams, where the callers impersonate help desk engineers from legitimate software companies. According to a Microsoft survey of 1,000 English language computer users back in 2011, 15% said that they had received one or more of these calls, and 22% of those who had gotten a call were tricked by the scam and paid an average of $875.00. If you do the math, you will see how somebody sitting at a desk in some remote part of the globe can rake in well over $2,500.00 simply by making 1,000 random phone calls. That dollar amount is only the haul from the bogus fees that they charge, earnings which could pale in comparison to what they can earn from the malicious software that they will install on your computer or the subsequent sale of your credit card number! The malware that they install is designed to harvest anything of value on your computer – including passwords, sensitive information and access credentials to things like your online banking and tax returns.
Continuing with the Microsoft report, 79% of those who were victimized by one of these scams reported some sort of financial loss, with 17% discovering money withdrawn from their bank accounts, 19% reporting passwords stolen, and 17% becoming victims of identity theft. A majority of victims also incurred significant costs in subsequently having their computers repaired or replaced after the experience.
To prevent this from happening to you, keep the following in mind:
- Microsoft (or Apple or any other tech company) will NEVER call you to offer assistance. If you need assistance from one of these companies, you probably know how impossible it is to obtain. Rest assured that they will NOT be the ones trying to call you!
- Never allow anybody to run remote access to your computer, unless you totally trust that individual. Remote access allows a total stranger total access to your computer. There is far too much at risk.
- Never purchase any type of software service from somebody who approaches you on the phone.
- Do not trust Caller ID. It is very easy to spoof the phone number that appears on Caller ID, and thieves use this trick to make themselves appear to be legitimate. Although Caller ID spoofing is a violation of the Truth in Caller ID Act and subject to a penalty of up to $10,000 per violation, thieves laugh in the face of the law. (Feel free to file a complaint with the Federal Communications Commission, the regulatory agency that is responsible for enforcement, either online or by calling 1 888 CALL-FCC.)
If you are uncertain about a company, I always suggest performing a quick Google search from the company’s name followed by the word “scam” or “complaints”. In the case of Tech Zone Windows, a Google search for “Tech Zone Windows Scam” currently produced 2,970,000 search results.
To learn more, read the following Microsoft security bulletin:
https://www.microsoft.com/en-us/security/online-privacy/avoid-phone-scams.aspx
This post was written by Peter Pelland
Tags: Caller ID spoofing, FCC, Federal Communications Commission, malware, phone scams, remote access, spyware, tech support, Tech Zone Windows
Posted in Cyber Security, Scams |
The Future is Always Connected: Netflix Nixes Offline Viewing
January 28th, 2015
As online video- and music-streaming becomes more and more advanced, many service providers and media portals have begun to roll out offline caching for videos and music. From Soundcloud to Spotify to Amazon Prime and Google’s brand-new YouTube Music Key, service after service has started to allow its users to store media locally, allowing for its later consumption. This feature turns out to be especially important for users on slower or bandwidth limited connections, who can locally store media on a WiFi connection to avoid long waits or bandwidth surcharges.

With just about every service rolling out offline caching in some capacity or another, it seemed only a matter of time before the 800 pound video streaming gorilla in the room jumped on board. We’re talking about Netflix, of course. For a while now, rumors had been swirling that Netflix was planning to launch their own offline caching options.
Now, in the bright light of the New Year, these rumors have been unceremoniously dismissed by Netflix Public Relations Director Cliff Edwards. Techradar reports that Edwards bluntly stated that offline storage was “never going to happen.” Why is this?
Netflix, it turns out, treats the non-ubiquity of bandwidth and connectivity as a short term problem, one for which offline caching is nothing more than a quick band aid. Instead, Edwards predicts that within five years, bandwidth will be so cheap and universal that users won’t even remember that they ever wanted offline caching in the first place, and will regard local storage as an outdated and obsolete concept for technology.
This is a contentious stance for a company to take, since it essentially implies that Netflix is willing to offer an inferior service on the short term to save resources. Netflix seems willing to lose customers to whom offline storage is especially important. Amazon Prime streaming has been quick to affirm its commitment to providing consistent and universal service to its subscribers. Currently, offline viewing is available for Fire tablets, and Amazon has announced plans to extend this functionality to more of its devices in the future.

Perhaps the case is that Netflix sees itself more and more as a content creator in addition to simple media provider. Like a more traditional TV station, Netflix is devoting more and more of its resources to the creation and curation of original video content, and perhaps sees its future as focusing more on this division of business. Netflix has already announced aims to debut at least 20 more original series in the next five years and is currently heavily promoting its new period drama called Marco Polo, following the adventures of the medieval Italian explorer.
No matter what you make of it, Netflix’s surprising decision about offline streaming belies a confidence that internet infrastructure will continue to be developed. Based on history, this is a safe bet, though it also shows a surprising self-confidence in their place in the market. Netflix seems to believe their position is unassailable. It will be interesting to see if this is the case.
Nick Rojas is a business consultant and writer who lives in Los Angeles and Chicago. He has consulted small and medium-sized enterprises for over twenty years. He has contributed articles to Visual.ly, Entrepreneur, and TechCrunch. You can follow him on Twitter @NickARojas, or you can reach him at NickAndrewRojas@gmail.com.
This post was written by Peter Pelland
Tags: Netflix, streaming, wifi
Posted in Business Ethics, Cyber Security |
10 Ways to Avoid Identity Theft
December 19th, 2014
If you follow the news, you are aware of massive security breaches that have taken place at major retailers in recent months. And then there is the Sony Pictures nightmare that has been in the news this week. You are probably also aware that your own personal identity is at risk in so many ways. Short of withdrawing from society and moving into a cave or feasting off coconuts on your own private island, it is probably a good idea to take some reasonable precautions to help to prevent hackers from cloning your personal identity or making you a victim of cyber-crime. Here are a few precautions that will help you to survive in this threatening environment.

- Always choose a strong password. It should never be a common word or an easily recognized string of numbers like your phone number or birthday. Use a randomly generated string of at least 8 characters that include a combination of upper and lower case letters, numbers, and special characters such as ^, #, _ and $. Use a unique password for every account, avoiding the tendency to use a common password. My rule is that, if the password involves a secure account that allows online transactions, give it an extremely strong, unique password. If the account involves online banking, stock trading, or tax filing, make your password ridiculously secure.
- If an account (such as your online banking) uses security questions, choose the most bulletproof options available, not questions with answers that are commonly known. You want to go with things like your maternal grandmother’s middle name, not the name of the city where you were born.
- Steer clear of unsolicited e-mails and unknown websites. Never download a file from an unfamiliar site, and do NOT open attachments, click on links, or unsubscribe from unsolicited e-mails. Any of those actions can lead to the installation of spyware, malware, botnets or viruses on your computer.
- Look for secure sites and the https protocol. Be sure that the URL begins with https before EVER entering your credit card number for payment.
- Keep your computer and mobile devices clean by promptly installing updates for your hardware, operating system, software and Web browsers. To run old versions of any of these represents a high level of risk. If you are running a Windows computer, there will usually be daily updates, and a major pack of security updates is issued the second Tuesday of every month, commonly known as “Patch Tuesday”. These updates are essential to your online security.
- If your business conducts e-commerce or accepts online payments, you have additional responsibilities that could impact your customers. For example, an Internet security issue commonly referred to as POODLE was identified in October. If your Web server was running SSL V3 (an outdated version), visitors using Internet Explorer 6 (an outdated browser) were vulnerable to allowing hackers to gain access to their otherwise presumably secure connection.
- Be sure that your office meets PCI (payment card industry) compliance standards. Never keep records of your customers’ credit card numbers. If you ever have to write down a customer’s credit card information – for example, if you are provided with that information over the phone – do not leave your desk before that information has been completely destroyed in a cross-cut paper shredder.
- How do you recycle or dispose of old computers? If you simply give them away or pay a disposal or recycling fee at your local landfill, where does your computer go? What kind of data are you leaving behind on its hard drive … for somebody to later recover? Before you ever part with a computer, it is essential that you first totally wipe all content from its hard drive(s). You cannot simply delete files or format the drive and then think that your data is gone. It is essential that you use a disk wiping or data shredding application that supports the latest Department of Defense standards. Even then, you would be amazed at how much data will still remain recoverable, if you were a criminal and your computer was being used by law enforcement to gather evidence. In your case, you want to protect your personal data from a hacker, who could be across town or scavenging a cyber-landfill across the globe. Some of the best software to use includes Disk Wipe, Darik’s Boot and Nuke, and Hard Drive Eraser … all free downloads that can be easily found online.
- What did you do with that old broken office copier? Did you realize that nearly every digital copier, fax, or multi-purpose office machine built since 2002 contains a hard drive? Like most people, you have probably made copies of your tax returns, credit applications, and other documents that contain your social security number and other highly personal information. A CBS News investigative report from back in 2010 exposed this vulnerability and how easy it was for anybody to purchase a used copier and then have full access to the contents of its hard drive. In the report, used copiers were purchased at bargain prices from a warehouse in New Jersey (one of 25 throughout the country), some of which contained classified law enforcement and private health records. The lesson learned was that, if your office has an MFP (multi-function peripheral) device that is at its end-of-life, take measures to ensure that its hard drive is destroyed.
- Finally, every computer in your office and every mobile device that you own should be running the latest version of a robust anti-virus software package that will be continually updated, typically several times per day. Sadly, the most common anti-virus products that come pre-installed on many computers or sold over the counter at office supply and computer stores are highly ineffective. I use (and highly recommend) Avast, a full-featured security suite for Windows computers, Macs, and the full range of mobile devices. It is available as a free download, with free updates (although, if you are not careful, you might click on a link for a paid upgrade that you do not need.)
If you know anybody who has ever been the victim of cyber-crime or identity theft, you know how important security measures such as these can be. If you were unfamiliar with one or two of these ten security tips – and implement the recommended precautions – you will be on your way to enhancing both your personal security and that of your business.
This post was written by Peter Pelland
Tags: anti-virus software, cyber security, data shredding, data wiping, e-commerce, hacking, online payments, PCI compliance, secure sites, security questions, SSL, strong passwords
Posted in Cyber Security |
|


















